
We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better. For example, the deep web is often a platform used by political activists who own a blog. But it also contains other news and religious sites, private discussion forums, and medical records.
Legal Uses Of The Dark Web

During our testing, we ran Tor over Proton VPN on both desktop and mobile. It handled multiple tabs inside Tor without slowing to a crawl, even when pulling text-heavy .onion sites and small downloads. NordVPN runs on AES-256 and ChaCha20 encryption, has a no-logs policy independently audited by Deloitte, and offers obfuscated servers for countries that block Tor or VPN use altogether. We stress-tested it using Tor over VPN, then flipped it and ran VPN over Tor, both held up without any weird breaks or traceable info.
What Are Onion Sites And Dark Web Websites?
The dark web is the hidden section of the internet that can’t be found on regular, surface web search engines. To access the dark web, one would need to use a special anonymous browser called Tor. Tor provides users with a higher level of privacy, which is particularly attractive to threat actors, cybercriminals, hackers, and government operatives who want to keep their identities secret. In addition, even if the Tor node fails, your data won’t be exposed because the VPN’s encryption still holds up. As mentioned, we recommend using a safe provider like NordVPN, which also offers Onion Over VPN servers perfect for accessing the dark web safely.
How It Works: Tor Over VPN

The value of the information can vary greatly depending on what’s being sold. Full profiles, or fullz, may come with a name, Social Security number, date of birth and account numbers and could cost around $8 to $30 each. Complete medical records can be particularly valuable to identity thieves, and may go for up to $1,000. Cryptocurrencies, such as Bitcoin, are the preferred means of payments as these also help keep buyers and sellers anonymous. For example, randomly clicking a link can land you in extreme content, such as child pornography, which is a serious criminal offense to access.
Why Use The Tor Browser With A VPN
It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. The platform is protected from government interference and malicious attacks to protect the user. In addition, it ensures that no record of communication is stored. That doesn’t mean it’s impossible to track users on the dark web. If you log into personal accounts on the dark web or visit websites with tracking scripts, then your activity may be tracked. Similarly, unless you’re using a VPN, your IP address will be visible to the first relay node you connect to.
Use Active Monitoring Of Financial And Identity Theft
As mentioned earlier, many websites consider Tor suspicious and block users entirely. Sometimes, you can access a website but won’t be able to login on your Tor browser. Likewise, some websites allow Tor, but with frequent Captchas that can be annoying. Tor doesn’t support plugins because they introduce security risks. Malicious actors often target browser plugins to steal website credentials or install malware on unsuspecting devices, so Tor sidesteps these risks altogether. You can also use DuckDuckGo to find onion sites across the Tor network.
Step 2: Download And Verify The Tails OS Image
As opposed to the previous situation, here, you’re first connecting to Tor and then the VPN. Not many providers support this, so a manual and sometimes tedious configuration is needed. NordVPN and many other providers offer Tor Over VPN or Onion Over VPN – whatever you want to call it.
We’ll navigate this intricate maze with you, uncovering its secrets while ensuring your online safety. Privacy-conscious users, including journalists and political activists, use the dark web to communicate securely, especially in oppressive regimes. While Bitcoin remains the most accepted currency on darknet markets, its traceable ledger has driven demand for alternatives. Privacy‑focused coins like Monero and Zcash offer stealth addresses and shielded transactions, making forensic blockchain analysis far more difficult. In 2025, darknet vendors increasingly demand Monero for high‑risk transactions, and new wallets now integrate atomic swaps for seamless conversion between currencies. Three common options—VPN‑only browsing, I2P and Freenet—offer different trade‑offs.
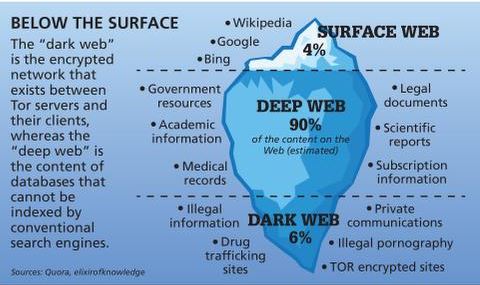
Tor and VPNs mask your network path, but a single careless click can still expose your identity. Follow these best practices every time you venture onto the dark web. When you envision the dark web, it may conjure up images of hackers trading stolen Social Security numbers or drug dealers advertising their products online—and that’s not completely wrong. While the dark web can be a helpful tool for sourcing legitimate products or ensuring private communication, it’s also a hotspot for illegal internet activity. The dark web is a part of the internet consisting of hidden sites that aren’t indexed by conventional search engines. It will route your traffic through multiple servers instead of one, making tracking your data and activities even harder.
- Other search engines like Haystak boast millions of indexed pages and advanced filtering options.
- I recommend using the Tor Browser with a good VPN for an extra layer of privacy and security.
- Some alleged services like the professional “hitmen” may just be scams designed to profit from willing customers.
- Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook.
- Absolutely no one knows who’s surfing on the dark web, who is selling, who is buying or anything like that – as long as you take the correct safety and online privacy precautions.
- You should never trust websites and forums on the dark web with your personal information.
Because of the dark web’s association with illicit activity, your use of Tor may be tracked by your ISP, drawing unwanted scrutiny to your browsing behavior. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia. The subreddit r/deepweb is a good starting point for asking more experienced users about how to search the dark web and deep web for the content you want. Lastly, The Hidden Wiki is a collection of dark web links — but the links may not work and can lead to dangerous websites. Surface web search engines can’t access the darknet, but specialized dark web search engines can help you find what you’re looking for. DuckDuckGo is a popular privacy-focused search engine that doesn’t track you across the web.
Importantly, not all users of these spaces are criminals—some are security professionals, journalists, or researchers trying to understand threat actors or investigate breaches. For instance, several major media organizations, including ProPublica and The New York Times, operate mirror versions of their websites on the dark web. These allow individuals in countries with strict internet censorship to access uncensored news and report safely to journalists without fear of retaliation. Some governments actively monitor or block Tor traffic, and Tor use can raise suspicion even when not used for illegal activities.
In his free time, Gannicus enjoys uncovering thrilling adventures and traveling around the world. Your Internet service provider, or ISP, is your gateway to the Internet. While a website can’t identify you or an ISP can’t decrypt your internet traffic; still, they can still see you using Tor, which can draw some unwanted attention and raise suspicions. Many turn to the dark to grab such medications with its private and secure networks. Some common pain relievers and sleeping pills available in the EU are illegal in various Middle East and Asia countries. The dark web has several convenient uses, which are not all basic.



