Automatic payments get declined, travel plans get disrupted, and sorting everything out with the bank can take hours. Sponsored content is written and edited by members of our sponsor community. This content creates an opportunity for a sponsor to provide insight and commentary from their point-of-view directly to the Threatpost audience. The Threatpost editorial team does not participate in the writing or editing of Sponsored Content.
Which Darknet Markets Accept Zcash
This adaptability underscores the ongoing challenge faced by financial institutions in combating the ever-evolving threat of dark web credit card marketplaces. Much like the situation after Silk Road was taken down, out of the ashes of Joker’s Stash, we have seen dozens of new carding data providers crop up, some specializing in particular regions or types of card data. Over the past decade, Joker’s Stash emerged as one of the most infamous dark web marketplaces, gaining notoriety for illicit transactions and offering a plethora of stolen financial data. The platform, distinguished by the sophistication of its administrators, left an indelible mark on the cybercrime landscape, and became the central marketplace for stolen card data, outclassing all competitors.
In recent years, I’ve observed some shifts in how carding is carried out—changes that mirror broader developments in both technology and threat intelligence research. Notably, cryptocurrency has become a valid option for carding operations, whether through exploiting stolen crypto wallets and accounts or using stolen credit card details to purchase cryptocurrency. There’s an underground ecosystem where sensitive data is bought, sold, and traded—not just on the dark web, as you might expect, but also on publicly accessible websites, channels, and forums. Among these are platforms dedicated to carding—a cyber crime niche centered on the large-scale use and abuse of stolen credit card information.
Taking Back Control: Protecting Your Business
Engaging in carding is a criminal offense that can lead to imprisonment and hefty fines for perpetrators. After significant regulatory fines on challenger banks for weak financial crime controls, Kate Robinson of Avyse Partners identifies the top problems and potential solutions for such firms. Once they had access to the victim’s account info, scammers would estimate their wealth to gauge the types of purchases they could make with the card.
Impel Global: Transforming Financial Messaging And Payments Through Blockchain Precision
- Opt for reputable and trusted payment gateways that offer strong encryption and advanced security measures.
- According to the United States Attorney’s Office, the ring of thieves obtained the credit card information on the dark web, and used that information to create their own cards.
- Computer scientist Ian Clarke developed the project, allowing for people to visit the internet anonymously without fears of being tracked by authorities or governments.
- This article delves into the intricate web of cybercrime, exploring how credit card details are leaked, sold, and exploited on the Dark Web.
- The shop offers stolen card data from around the world for as low as $0.15 per item and uses verification and automated checks to check the validity of the cards people put up for sale on the platform.
While this is convenient, it places your credit card information at risk of being exposed in public data breaches, so it’s best to never save it on websites. They are used by mid-level and highly experienced fraudsters who know how to use them effectively. Gathering resources is usually the first phase for criminals who want to commit fraud. Obtaining good quality materials is always an important part to being a successful craftsman – it is no different for those involved in carding fraud. As Figure 2 demonstrates, one of the largest dark web marketplaces, Alphabay, runs its own credit card shop as an additional feature of the site.
Dark Web Prices For Stolen PayPal Accounts Up, Credit Cards Down: Report
There are plenty of reasons people won’t always get their money back, and dealing with the fallout can be stressful at the least and traumatizing at the worst. Plus, scammers do get caught—often ending up with a lengthy prison sentence or hefty fine. WeTheNorth is a Canadian market established in 2021 that also serves international users.
What Stolen Cards Are Used For
Financial data can leak in many ways—through phishing attacks, data breaches at online services, or poor account security. Even in regions like the EU, where banks are legally required to implement strong customer authentication, criminals continue to find ways to bypass these safeguards. Dark web credit card fraud poses serious risks to consumers and businesses alike. Discover the pros and cons of using credit cards or card for purchases, including benefits and risks, to make informed financial decisions.
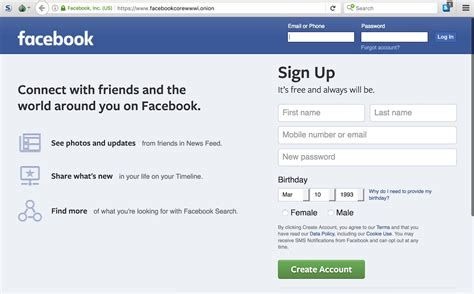
Contrary to popular belief, most carding platforms no longer hide in the dark web (i.e. the Tor network). The sites I’ve evaluated this year all had clear web addresses—with ‘.onion’ versions available for some of them. Learn the basics of credit card cards, including features, fees, and rewards to make informed decisions about your credit card usage.
Developer Verification: A Promised Lift For Android Security
A vast majority of bank and credit card apps offer notifications and alerts for questions about suspected fraud. The Tor network provides powerful tools for enhancing online privacy and anonymity, but these benefits come with certain trade-offs. Tor Network, short for “The Onion Router”, is a network consisting of volunteer servers that encrypt Internet traffic and route it through multiple nodes. This technology makes it very difficult to track the identity or location of users.
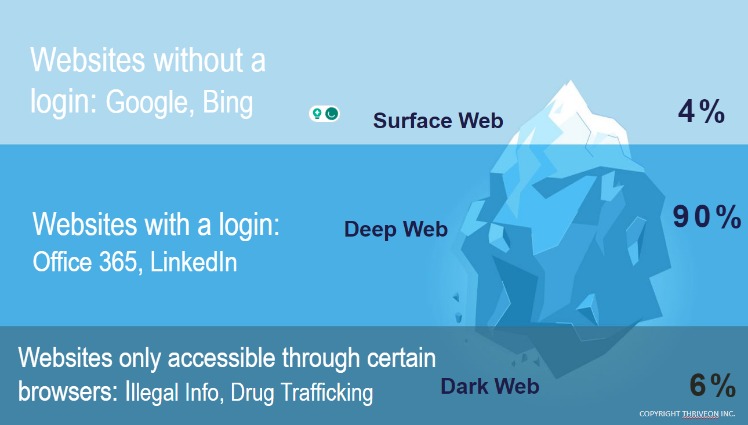
Once upon a time, bandits and thieves wielded masks and ransom notes to steal people’s hard-earned money. Just as many of our financial transactions and banking activities have moved online, so have the more sophisticated forms of theft. When it comes to financial crime, the “dark web” — the encrypted, underground network of websites that exists beneath the “surface web” — is a veritable playground for fraudsters. You’re probably wondering how things like a PayPal account login or credit card details end up on the dark web.
Staying Safe Online
Launched in September 2022, Torzon Market operates on the Tor network and features over 11,600 illegal products, including drugs and hacking tools. It enhances buyer transparency by importing vendor feedback with PGP proof. Torzon offers a premium account option for additional benefits and is valued at approximately $15 million, accepting payments in Bitcoin (BTC) and Monero (XMR).
Its interface is easy to navigate, and it has a reliable escrow system, as well as allowing payments with Bitcoin and Monero. All of this has made it one of the most reliable markets still active in 2025. The sooner you become aware of compromised information, such as stolen credit card numbers on dark web, the faster you can take steps to mitigate damage. Rapid response can prevent unauthorized transactions, minimize financial losses, and protect your customers’ trust in your business.
OUR PLATFORMS AND BRANDS
Network segmentation is absolutely critical for businesses handling card data. One particularly interesting detection method involves monitoring dark web markets themselves. You may have never been to the dark web — but there’s a chance your credit card information has. As data breaches become more common, and scammers grow more sophisticated, this is a reality many people are having to contend with.