Even if you report the fraudulent activity quickly and limit your losses, you may still face the issue of bounced checks or being late on payments, Krebs says. Many tracker apps link directly to bank accounts for up-to-the-minute info. They show recent purchases, account balances, and spending trends all in one place. Tracker apps offer a powerful way to keep tabs on credit card activity. These tools scan transactions in real-time, flagging any suspicious charges instantly. 1 This quick notice helps spot fraud fast, before major damage occurs.
Darkweb Market BidenCash Gives Away 12 Million Credit Cards For Free
– Take note of any patterns or recurring issues mentioned in the feedback, such as inconsistency in card quality or lack of response from the vendor. – Examine the feedback relevance and authenticity by considering the comments and overall sentiment expressed by previous buyers. – Look for a substantial number of feedback and ratings to ensure a more accurate assessment of the vendor’s performance. The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown. If you ever decide to explore the dark web, protecting your identity is crucial.
Largest Darknet Stolen Credit Card Site Closes

This ensures that messages, transactions, and data exchanges remain confidential and protected from interception. Dark web browsers and search engines do a lot of work to mask user identities, but you’re never completely untraceable. Not to mention that anonymity safeguards won’t protect you from other threats like hacking and malware.
Top Strategies For Risk-Based Transaction Monitoring
This post will discuss deep and dark web credit card sites, specifically the top illicit credit card shops. Carding has long been a prevalent form of online crime—and it remains a serious threat. One such protection is the use of anti-fraud tools, such as F‑Secure Total, our complete online security solution.
Using Tracker Apps To Monitor Your Card Data
The Cracked Dark Web forum hosts posts on exploit development, zero-day exploits, user logins, and cybersecurity. Cracked is not an illegal platform and is used by cybersecurity experts and penetration testers. Dark web forums use advanced encryption techniques to secure communications between users.
It’s believed that the administrator behind Joker’s Stash came away a “Bitcoin billionaire”. See my tips and best picks on how to protect yourself from identity theft by searching “identity theft” at CyberGuy.com by clicking the magnifying glass icon at the top of my website. The operators of BidenCash have caused significant harm to millions of victims whose personal and financial information has been compromised.
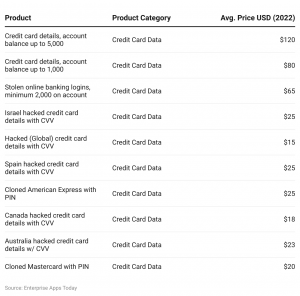
The stolen credit card records include credit card and owner details, including credit card number, expiration date, CVV number, holder’s name, country, state, city, address, zip code and email address or phone number. In our research of the data of 1M leaked credit cards on the Dark Web, we analyzed the leaked email addresses to gain a better understanding of the risk. Additionally, fraudulent charges can lead to overdraft fees, late payment penalties, and damage to credit scores. These financial losses can have a lasting impact on victims’ financial stability and may require extensive efforts to resolve the issue and regain control over their finances. To avoid such losses, it is crucial to regularly monitor credit card transactions, report any unauthorized charges promptly, and take proactive steps to protect personal information. Additionally, phishing scams and malware-infected websites are utilized to trick unsuspecting victims into providing their credit card details unknowingly.
Picus Blue Report 2025 Is Here: 2X Increase In Password Cracking
If the company you’re buying from doesn’t have your sensitive card information, neither will hackers that hit that merchant with a data breach. Holders of any credit cards, whether you know if they have been compromised or not, are advised to monitor bank statements for any suspicious or unusual activity. Strong passwords and security tools add extra layers of defense against cyber threats.
- Some vendors include access to a SOCKS5 internet proxy to help buyers avoid being blacklisted.
- Risepro, which primarily focuses on stealing banking card details and passwords, is another fast-spreading infostealer.
- Exploring the realm of credit card transactions on the Dark Web is a journey into a dangerous and illegal world.
- Early detection lets you take immediate action to protect your finances, such as alerting your bank or requesting a new card to avoid further risks.
- In particular, companies involved in handling large amounts of consumer data should be aware of just how easily that data can be monetised — and abused — online.
- Forums can serve as platforms for these individuals to coordinate activities, share information, and launch politically motivated attacks.
B List Of 12 Onion Websites
This continuous exchange of information drives the rapid evolution of cyber threats. The global nature of the dark web complicates law enforcement efforts. Cybercriminals operate across borders, exploiting differences in legal jurisdictions to avoid prosecution.

Compared to harvesting phone numbers or email addresses, carding demands more risk, and potentially, more reward. Contrary to popular belief, most carding platforms no longer hide in the dark web (i.e. the Tor network). The sites I’ve evaluated this year all had clear web addresses—with ‘.onion’ versions available for some of them. Mitigate risk of a cyberattack with 24/7 incident and health monitoring and the latest threat intelligence. Dark Storm Team is a politically motivated group that uses Telegram to broadcast its cyber activities.
Ensuring Strong Encryption And Secure Data Storage
Today, although threat actors broadcast their illegal activities via applications such as telegram, dark web forums are still one of the current content sources. According to the analyses made by ThreatMon analysts, there are important findings detected and obtained from dark web forums as the first source. With the detection of exploits, zero days, malware, etc. content obtained from dark web forums, proactive intelligence is developed by analyzing current malware. Back in the day, carding forums were the busiest of online crime hangouts, selling packs of stolen credit card data to anyone with the cash. That was then; now, you are more likely to find a roaring trade being made on the dark web in the likes of stolen passwords and account credentials, phishing exploit kits and malware-as-a-service platforms. A new report has revealed that the B1ack Stash crime forum has just given away more than a million stolen credit cards for free.
How To Buy Credit Cards On Dark Web
This proven technology, seamlessly working in the background, analyses transaction data and authenticates users in real-time, ensuring only legitimate transactions proceed. Stolen credit cards are often used to make purchases at specific sites that don’t have protections against fraud. Once you find a forum or market that offers the service you’re looking for — such as stolen passports — signing up for them is not unlike creating an eBay account. The main difference is that purchases are made with cryptocurrencies, and quite often such sites are far more secure than their clear web counterparts. Passphrases, distributed denial-of-service (DDoS) protection pages, and multifactor authentication are all quite standard on many darknet marketplaces. Some criminals organize stolen card data by ZIP code, according to Novak, “because it makes it harder to conduct fraud detection,” he says.



