
Reddit is also a valuable resource for finding the dark net or deep website you’re looking for. Instead of “.com” or “.org”, dark web addresses can be distinguished by the top-level domain, “.onion“. Based on Firefox, the Tor Browser lets you surf the clear and dark web. Ensure you download the Tor Browser from the official website to avoid downloading malware, spyware, or other viruses to your device. The easiest way to access Tor is through a special browser known as the Tor Browser. You might want to hide your Tor Browser download using a VPN and your existing browser’s private/incognito mode.
Then, try LifeLock free for 30 days to help find out if your personal data is leaked on the dark web. The main contribution of these studies is to shed light on commonalities and differences between online and conventional black markets and to explain recent trends such as the commoditization of criminal services. Some studies investigate the relationship between OBMs technologies and their social organization. Their focus has been mostly concentrated on functioning and operations over limited time spans.
First, Install A Reliable VPN
This .onion link makes it impossible for hackers to impersonate your profile. The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers.
Dark Web Marketplaces: The Trade Of Illicit Goods And Its Impact On Cybersecurity For Businesses
“This shift complicates law enforcement’s ability to track illicit financial flows, pushing agencies to invest in new blockchain forensic tools and cross-chain analytics,” Kurrie says. AI has the ability to accelerate the scale and sophistication of cyber attacks and it’s starting to be incorporated into tools and services on the dark web. Ransomware as a service, stealer malware as a service (SMaaS), and phishing-as-a-service operations are thriving and helping fuel illicit add-on services.
Even with the increase in law enforcement pressure, the dark web market still achieved a revenue of $2 billion in 2024. Therefore, as long as this dark part of the internet exists, these marketplaces will flourish and emerge. Together the three mechanisms describe the generative forces of the OBMs infrastructure. Each individual mechanism fails in producing this outcome independently.
- Use it to search the normal internet from the privacy of your Tor Browser.
- Its intuitive interface and advanced search features make it easy to find local and global products.
- Hydra is listed as a Wayaway Partner on the forum’s footer along with Hydra logos, market links, and various digital advertising scattered across the forum.
- It brings in vendor reviews from other places and verifies them using PGP signatures, so buyers can feel a bit more confident about who they’re dealing with.
- We deliver contextualized, actionable intelligence through our dedicated platform or API integration, ensuring that you can respond effectively to darknet threats.
- Our model adds a process view to explain the role of social media in e-commerce (Huang & Benyoucef, 2013).
Torrez Market
- Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info.
- Although the social application is known for collecting data on its platform, it does not like sharing the information with others.
- OBMs serves as digital innovation hubs for criminal communities and can be used to discover new schemas of illegal activities.
- Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites.
“But much of this appears to be driven around a need for criminal threat actors to get convenient access to quick payments from victims in order to support further operations,” he adds. AI-as-a-service (AIaaS) platforms offer many of these capabilities that lower the barriers for cybercriminals to carry out these attacks. So far in 2025, Nightwing has tracked more than 90 ransomware and data extortion groups active in just the past six months, with 16 of these groups having leak sites that are only about 90 days or less old. As dark web operations fragment into smaller, granular communities, cybercriminals are developing their own identities to market their activities and illicit tools. Initial access brokers (IABs) are thriving, selling entry points into corporate environments, which are then monetized by ransomware affiliates or data extortion groups.
Why Small And Mid-sized Businesses Are A Huge Target For Cyber Attacks

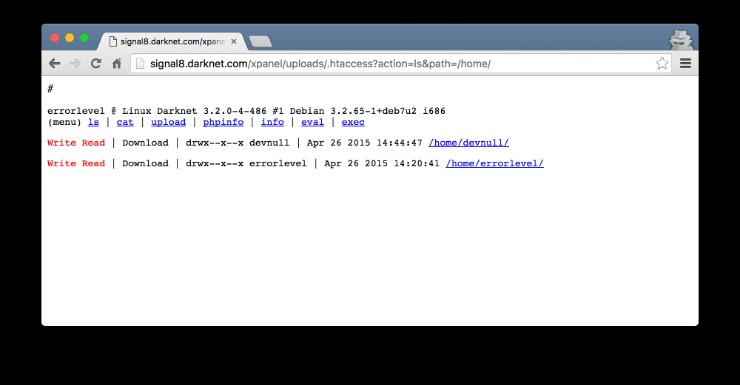
This archive provides an excellent investigative referential database for prominent darknet vendors and their aliases. Hacking and cybercrime forums on the dark web are spaces for newbie hackers to ask questions, veteran cybercriminals to share their expertise, and buyers to find sellers. Cybercrime services are more commonly sold through marketplaces, but you can usually find someone offering hacked servers, computer logins, and stolen data on such forums. The two mechanisms described above are the basic forces of OBMs infrastructure, making operations possible despite the lack of transparency, law enforcement control, legal protection and centralized governance.
Operations
So, if you want to know how to access the dark web safely, you need to understand that the vast majority of the dark web, or dark net, is only accessible through the Tor browser. It’s like an iceberg – The visible tip above water, known as the “surface web” represents the familiar, searchable content. But lurking beneath lies the expansive, mysterious “deep web” or“dark net” – the gigantic submerged part that remains invisible to standard searches.
Is There A Future For Dark Web Marketplaces?

Since its inception, the Internet has provided users with an infrastructure enabling different forms of interactions. Group communications, private messages and file sharing are fundamental functions provided by many tools with different levels of sophistication. Online communities whose members are concerned with anonymity have different options to interact without disclosing their real identity. An example is Reddit.com, a popular social news aggregator, established in 2005, which also hosted from 2010 until 2018 a subcommunity of approximately 20,000 members focused around OBMs related matters. Previous research can be grouped into three streams as illustrated in Table 1. A first stream of literature is focused on the interactions of actors performing illegal activities on OBMs.
OMs act as intermediaries by directly matching supply to demand and suggesting possible transactions or by providing easy-to-use search functions through which users can find transaction partners. Via the orchestration of transactions, digital platforms create two-sided markets (Armstrong, 2006) that leverage cross-side network effects. Using a reliable VPN provider helps keep you safe when you access marketplaces on the dark web. A VPN encrypts the data traffic and keeps your activities private on the dark web. It also masks your IP address, making it difficult for government agencies to monitor or track your activities.
However, such shocks do not affect the existence of OBMs (Décary-Hétu & Giommoni, 2017). Dark web marketplaces are like the hidden corners of the internet where illegal activities take place and even thrive. These markets operate on the dark web, a part of the internet that’s not indexed by traditional search engines and requires special software, like Tor, to access. Here, you can find anything from stolen credit card information and personal data to illicit drugs and counterfeit goods. Dark web marketplaces are online platforms operating within the dark web, where individuals trade illicit goods and services while preserving their anonymity. Unlike traditional e-commerce websites, these marketplaces rely on encrypted networks like Tor (The Onion Router) and cryptocurrencies such as Bitcoin to conceal user identities and transactions.

A favorite of journalists and their anonymous sources, SecureDrop makes it easy to share confidential information without revealing your identity. Many news publications, like the ones listed above, have a SecureDrop on their .onion sites. The internet’s favorite alternative to Google made a name for itself by not logging your search activity yet still providing decent results. This focus on privacy makes it the Tor Browser’s default search engine and one of the best onion search engines. Search engines on the dark web are a bit of a contradiction because dark web sites by definition are not indexed by traditional search engines.
With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
A Dark Web Search Engine
After the seizure of Silk Road, in the period from October 2013 until April 2018, we registered the existence of 122 marketplaces. During this period, 9 have been closed by LEAs and 42 have been closed by admins with an exit scam (sources T1 and T4 in Table 2). An exit scam occurs when an established business stops shipping orders while continuing to receive payments for new orders. Figure 3 reports the number of active marketplaces on Tor per months and 5 significant key events discussed below.



