It includes any page that you can find with a simple Google search. However, your access is limited to the information that the website’s administrator permits you to see. The key takeaway is that the dark web is part of the deep web, but they’re not interchangeable. As for the dark web, it’s intentionally hidden, encrypted, and made anonymous.
Step 7: Use Additional Security Tools
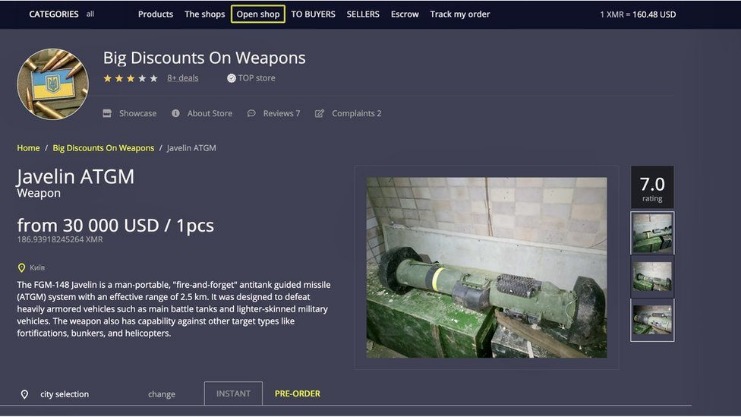
These sites can be used by both hackers and individuals looking to exploit vulnerabilities. Drugs are typically sold using cryptocurrency to maintain anonymity, and the buyers and sellers are often difficult to trace. These markets operate similarly to physical drug markets but are hidden from law enforcement through the use of the Tor network. Importantly, each node is representative of an additional layer of encryption. No node can track the complete path the traffic has taken, and more importantly, neither can anyone who finds it on the other side.
What Is The Dark Web And How To Access It?
So, to clarify again, this tutorial will cover how to access the dark web privately and safely – not the deep web. You can go on the dark web safely, use legal sites, and enjoy the experience without worries. In this tutorial, we’ll explain how to access the dark web in complete privacy and cover a few more important factors to consider before starting. As long as you are vigilant about your online activity, there aren’t any issues. The maximum trouble you can get into on the dark web is visiting political forums or marketplaces.
For Using The Internet Anonymously
Unfortunately, your ISP can see you are on Tor, which may restrict your connection. There are several misconceptions about the dark web, as many users use it for illegal activities. While VPN over Tor is a bit more complicated to set up, it protects you against malicious exit nodes. All data is routed from the exit node through a secure VPN connection.

Limit Tracking On The Tor Browser

Freenet is still an experiment designed to resist denial-of-service attacks and censorship. When you open your default browser, Freenet will be ready and running through its web-based interface. Note you should use a separate browser than the one you normally use to help ensure anonymity. For a number of technical reasons, it’s much faster and more reliable than Tor. The peer-to-peer routing structure is more advanced, and it does not rely on a trusted directory to get route information.
What Is The Dark Web & How To Access It Safely In 2025
Combining it with VPN and good digital hygiene improves security. Onion links are URLs that end with .onion and can only be accessed through the Tor network. Accessing the Dark Web using the Tor Browser is not just about exploring hidden parts of the internet—it’s about understanding privacy and cybersecurity in the modern world. Journalist in India → Uses Tor to access a whistleblowing portal → Submits information anonymously while protecting their identity. Install AVG Secure VPN to encrypt your internet connection and protect your privacy wherever you go on the web. Download AVG Secure VPN to encrypt your internet connection and protect your privacy wherever you go on the web.
Learn how to safely access the dark web with this comprehensive guide for beginners. Most URLs on the dark web have unrecognizable names, so it’s easy to fall for this trap — putting your private files, financial data, keystrokes, and other personal information at risk. Social engineering tactics are also common, where bad actors try to get you to willingly give up sensitive information, like login details, financial information, etc.
How To Stay Safe While Using The Dark Web
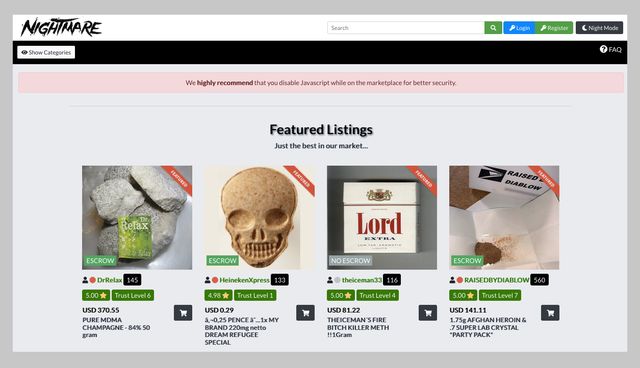
There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale. Not every visitor is a criminal, but this is where most cybercrimes begin. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything.
The CSO Guide To Top Security Conferences
Users’ internet traffic is sent through an encrypted network of volunteer-maintained relays around the world. This makes it very difficult to trace the original users’ identity. Tor’s anonymity function is used by everyone from human rights workers and journalists through to drug and arms dealers.
The Safer level enhances security by disabling certain features, and the Safest level entirely blocks scripts, which may impact some functionality. Once connected, you should be redirected to the browser’s homepage. But, to get there, you need a special kind of browser because the Dark Web is all about keeping things under wraps with encryption. If you want to dive into the Dark Web using your smartphone, I’m here to debunk the myths and walk you through it step by step. Ready to start your undercover internet adventure on your Android or iPhone? Join millions of users who trust ForestVPN for privacy and unrestricted internet access.
What Should I Do If I Encounter Suspicious Links On The Dark Web?
Sci-Hub is a massive database that eliminates the barriers to getting scientific knowledge. It contains millions of scientific research documents from around the world. The site seeks to liberate information by making it free to individuals and institutions. ProPublica is a popular online publication that won five Pulitzers in 2016.
Once you log in, you’re moving beyond the surface web and into the deep web. PCMag is obsessed with culture and tech, offering smart, spirited coverage of the products and innovations that shape our connected lives and the digital trends that keep us talking. There are a lot of misconceptions about it, but we’ll answer that question once and for all in this guide. We’ll also discuss why it’s dangerous and why you should inform yourself about the dark web even if you don’t plan to be on it. There are lots of perfectly legitimate reasons you might want to access all that shady content.
- As you might expect, Bitcoin is the top cryptocurrency being used on the Dark Web.
- This guide will teach you how to install the Tor Browser in Windows easily so you can access the Dark Web or browse the web anonymously.
- The features make NordVPN viable for accessing the dark web as your IP address can’t find out that you are using Tor.
- Copy your desired onion URL and paste it into the address bar at the top of the screen to begin searching on the dark web.
They use a scramble naming structure that combines a string of letters and numbers to create URLs that are impossible to remember. Anonymizing browsers are banned in some countries like China and Russia. Moreover, given the nefarious nature of the dark web, some government agencies may set up Tor gateways to monitor what’s happening on the dark web. If you’re intrigued and want a firsthand experience, follow this guide to learn how to access the deep web with an anonymizing browser. We’ll use the Tor browser for this guide, but any other browser that supports the Tor protocol will do.
Illegal Pornography
Dark0de alone had over 69,000 listings, while Torrez offered around 57,000.2 By far the most infamous dark web marketplace is the Silk Road. Let’s take a closer look at it to see just how dark the dark web can be. If you want to purchase something from one of the many dark web marketplaces, under no circumstances should you use anything other than cryptocurrency.

No one knows precisely how many dark web sites there are out there. Tor is designed to be resistant to web crawling but the number of active ones probably only number in the thousands. The deep web also includes most academic content handled directly by universities. Think of this like searching for a library book using the facilities’ own index files – you might have to be in the library to search there. This could include sites not automatically available to the public, such as those which require a password. Examples of this might be e-mail accounts or registration-only forums.



