
Confidential government files and pages tied to unlawful trafficking often get filtered out. Unlike traditional search engines, it doesn’t track or store personal information, ensuring your searches stay private. It’s a popular choice for users worried about online surveillance and data collection. The New York Times operates one of the biggest news sites on the Tor network, letting users access its regular news coverage with increased privacy and security. The onion site is especially beneficial for people in regions with heavy censorship or restricted access to media. Dark web websites are pages that exist on a part of the internet that isn’t indexed by traditional search engines like Google.
Comment 21
Yes, you can access the dark web on mobile — you just need the right app. Android users need to download the Tor Browser app, while iPhone fans should get the Onion Browser app. Unless you know where you’re going, there’s always some risk connected to clicking on dark web search engine links. Stay private with a tool like Surfshark’s Alternative ID to mask your contact details and use generated data on sites you don’t trust. ZeroBin’s onion address ensures your traffic is routed through multiple nodes, so it’s challenging for any third party to trace any message back to your original location.
Use a good VPN to stay away from danger and your risk factor will be very less. The numbered reference system used to catalog disclosed vulnerabilities and exploits is called the Common Vulnerabilities and Exposures (CVE) system. Ryan Montgomery is a professional hacker, who uses his skills as a cyber security expert and specialist to expose some of the worst people in the world. Yellow Sweet Spanish’s paler sister, White Sweet Spanish is characterized by cream-colored symmetrical bulbs with a sweet, mild flavor and crisp crunch. This beautiful short-day red onion is enriched with some disease resistance to botrytis and pink rot. The glossy, flat bulbs are firm in texture but mild in flavor, making this variety suitable for slicing and snacking.
Given the above threats, it’s a good idea to use Tor over a VPN to access the dark web. This space for private free speech also carries the risk of exposing you to harmful content. This makes Riseup a vital tool for people in oppressive environments or anyone concerned with online privacy. Since the organization behind it is independent, it’s fully user-supported and relies on donations to keep its site up and running. All of this underscores Riseup’s prioritization of users’ rights over business interests. It’s maintained by a volunteer-run collective from the USA that protects the platform from malicious attacks and pledges to support social justice and progressive causes.
How To Exploit Recycled Credentials With H8mail To Break Into User Accounts
If cutting onions tends to make you tear up, this is the variety for you. Dixondale Farms claims that Texas Super Sweet contains very little pyruvate, which is the chemical that causes our eyes to water when we slice into a juicy bulb. But that’s not all this short-day yellow onion has going for it–the large, flat bulbs average six inches in diameter and are ideal for slicing, cooking, or roasting. Known for both its bite and excellent storage capabilities (half a year or more) Red Creole is the perfect onion to use in spicy Cajun dishes.
The New York Times — Globally Recognized News Coverage
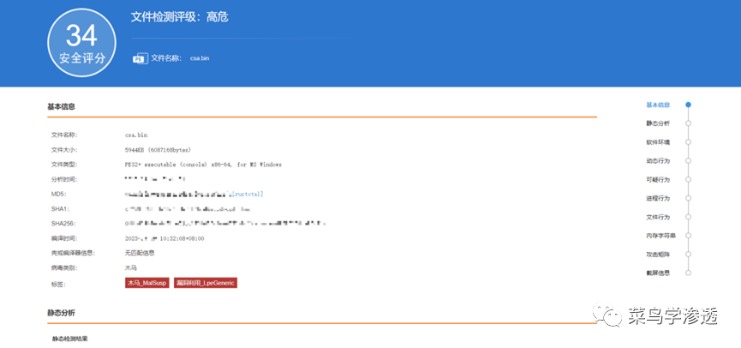
Over the last month, a darknet marketplace calling itself TheRealDeal Market has emerged; it focuses on brokering hackers’ zero-day attack methods. Like the Silk Road and its online black market successors, TheRealDeal uses the anonymity software Tor and the digital currency bitcoin to hide the identities of its buyers, sellers, and administrators. In some cases, these are offered on an exclusive, one-time sale basis.
While LockBit managed to rebuild its infrastructure, this new breach highlights the fragility of its resurrection. Apple’s iOS 26 and iPadOS 26 updates are packed with new features, and you can try them before almost everyone else. First, check Gadget Hacks’ list of supported iPhone and iPad models, then follow the step-by-step guide to install the iOS/iPadOS 26 beta — no paid developer account required. Once a common pantry item, these fruits disappeared when we started relying on global food transportation.
Broken Links
Although docker exists as a package for Debian, the latest version at the time of writing did not support v3 hidden services. That’s why I had to modify the Dockerfile a bit to install the latest version using the recommended way. I’m currently taking Prof. Florian Tschorch’s Network Security class and we had a lecture covering Tor and Onion services. All tor does is provide onion addressing and strong authentication with increased the observation costs for passive observers.

Mac For Hackers: How To Use Git To Clone, Compile, And Refine Open-Source Hacking Tools
While there are severalreports of scams occurring with private sales, the searchable public database is quite legitimate. Dive into a seed catalog and you’ll see that there are nearly as many onion varieties as there are tomato varieties. There are delicious heirloom onions and disease-resistant hybrid cultivars.
ZeroBin — The Secure Way To Share Your Pastes
Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren’t even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online. This yellow onion is characterized by large, globe-shaped bulbs and a sweet, mild flavor. Short-day onions start forming bulbs when days reach 10 hours in length. For this reason, short-day onions are ideal for warmer regions closer to the Equator–USDA hardiness zones 7 and warmer. Users can explore onion sites easily and search for content without having to know any specific onion links in advance.
- If you start short-day onions in the spring, the plants won’t have time to grow robust tops before transitioning to bulb development.
- Both exploit repositories have timestamps on their exploits, so let’s graph those.
- If you can’t find one close to home, consider starting one.
- Ahmia also discourages access to illegal content and promotes safer internet practices.
- With more than 45,000 exploits1, EDB exceeds 0day.today’s offering of just under 38,0002.
You’ll find articles on a wide range of topics, such as history, science, and culture — and that’s just scratching the surface. So take this guide as you explore where to go on the Tor Browser without risking your online security. As a gesture of goodwill and to assist those affected by our previous activities, we are offering free decryption software to all companies that have beenimpacted by our ransomware. Our goal is to ensure that you can recover your encrypted data without the burden of paying ransoms. Crt.sh is a website that allows users to search for SSL/TLS certificates of a targeted domain, providing transparency into certificate logs. We’re also ready to accept submissions for Demos, Workshops, and Policy.
Recommended Sites

Tor Metrics is a dark web site that keeps track of who’s using the Tor network and where they’re accessing it. It’s an interesting resource that translates Tor internet traffic levels into easy-to-digest stats. Riseup is available on the surface web, but its presence on the Tor network extends its privacy benefits by letting you use its services without exposing their real-world identities. You can access encrypted email services through the onion site without getting tracked. Accessing ProPublica via the Tor Browser gives users an added layer of privacy and lets them bypass restrictive government censorship.
It’s similar to Reddit or Quora but designed for anonymous users. Users can ask questions, share answers, and engage in discussions without revealing their identities. Riseup provides email and chat services that keep no record of your online activity.
- Stay private with a tool like Surfshark’s Alternative ID to mask your contact details and use generated data on sites you don’t trust.
- While there are severalreports of scams occurring with private sales, the searchable public database is quite legitimate.
- You have to go through something called Tor, or The Onion Router, which is a software enabling anonymous communication online.
- Cut into a Red Stockton onion and you’ll be met with concentric pink and white rings.
- Another way of thinking about onions is to group them based on their sensitivity to light.
Comment 13
This is especially important for individuals in regions where press freedom is restricted or where government surveillance poses risks to journalists and activists. It doesn’t track browsing habits or personal data and won’t expose a user’s identity or location. This makes it safer for those who can’t freely access certain content. While many dark websites appear sketchy, The New York Times is an exception. It offers reliable news coverage without exposing readers to harmful or illegal material. Explore the largest curated directory of cybersecurity tools and resources to enhance your security practices.
” That’s true, but we aren’t 100% sure how they arrived at that number. We believe they only exceed 38,000 if you include shellcode in the count. They actually dealt a lot with the traffic analysis problem, and had both a technical and financial model to encourage defense against it. It wasn’t perfect, but it would be more resilient to this stuff than Tor IMHO. It just had the disadvantage that latency was atrocious (for obvious reasons), and ultimately it turns out people don’t care about anonymity. Zero days are known, exploited and used all the time by all sorts of black hats, govt institutions etc.



