
Companies must implement strong data security measures, employ encryption, and monitor for data breaches to protect customer and employee information. Transactions within dark markets predominantly involve cryptocurrencies like Bitcoin, Monero, or Ethereum. These digital currencies provide a degree of anonymity, as transactions are recorded on a public ledger but do not directly link users to their real-world identities. Launched after the takedown of AlphaBay in 2021, Abacus Market has rapidly risen to prominence.
- Unlike traditional TLDs, servers using the onion TLD are more difficult to locate.
- Some chase banned goods—like a coder I met hunting censored PDFs—others love the mask it offers.
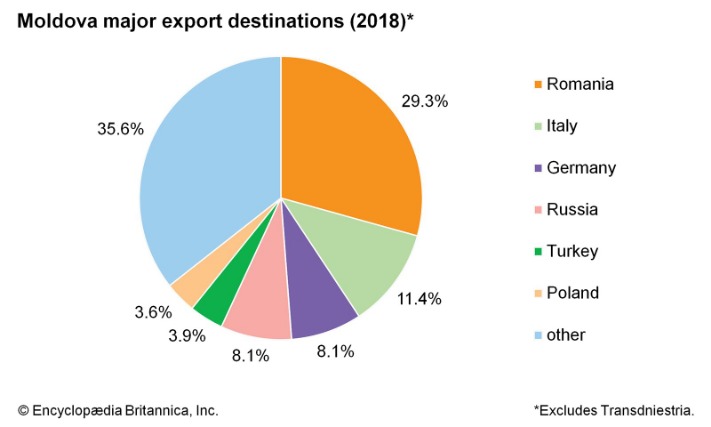
- Moldova is a source and transit country for synthetic drugs, with criminal networks producing the drugs for export into Ukraine and Russia.
- You can pay through Monera and Bitcoin using the escrow system or the traditional market account after making a purchase on this shop.
When you use it, all the web traffic automatically routes through Tor. If the operating system detects any non-anonymous connection, it blocks it, thus ensuring maximum online protection. Further market diversification occurred in 2015, as did further developments around escrow and decentralization. Manual monitoring of the dark web is inefficient and risky due to the sheer volume of data involved. Organizations need automated dark web monitoring to prevent cyberattacks.
What Is Darknet?
This can include everything from full names, email logins, and passwords to credit card details, social security numbers, and bank account information. The cybercriminals trade even sensitive documents, such as medical records, passport information, and driver’s licenses. As we mentioned earlier, not everything sold on dark web markets is illegal. As terrible as its reputation may be, some vendors sell legitimate goods or services. Some customers even use the dark web to make anonymous purchases, especially in areas where privacy is a huge concern.

Tech Keeping Darknet Markets Alive
Below are the best marketplaces on the dark net that we hand-picked after going through multiple shops and doing extensive research. Since the dark web can be accessed through the Tor browser, use a VPN with the Tor browser to ensure increased protection. A VPN hides the fact that you’re using Tor, which is blocked in some countries and always raises doubts because of its criminal reputation.
Why Monero Over Bitcoin?
Darknet marketplaces like to exist on the dark web because it offers a service that the regular internet, or more accurately, the “surface web,” does not. N 2025, dark web websites frequently change domains and are often short-lived. Accessing them may require .onion links and the Tor browser, but caution is advised due to legality and cybersecurity risks. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024.
Shuttered Dark Web Marketplaces

It has been in operation for more than a decade since its debut in 2014. Brian’s Club is one of the best place to buy stolen credit card info, including CVVs, dumps, and even full account packages without revealing your identity. Of course, not all the popular and widely-used dark web sites and things like marketplaces on the dark net are illegal. Some use them due to privacy concerns, such as journalists talking to informants or whistleblowers, while others may simply want to protect their confidential information from observation or tracking. Nevertheless, most people on the internet do not need to communicate or venture into the dark web.
These shifts tie into how markets like these are evolving—check them out below. Jumping into the dark web can feel like a maze, but it’s pretty doable once you’ve got the basics down. First off, you’ll need the Tor Browser—think of it as your ticket in.
Authorities Have Taken Down The Dark Web’s Largest Illegal Marketplace
In 2022, for example, BidenCash was linked to the breach of over 1.2 million credit card records. One of the distinguishing features of Fresh Tools Market is its focus on providing up-to-date, freshly obtained tools and credentials. Founded in 2020, Cypher Market has carved out a niche on the dark web by focusing on cybercrime products. Mega Market, established in 2016, experienced a surge in popularity following the takedown of the Hydra market.
Criminal Justice And Security
In exploring the top 10 dark-web marketplaces in 2025, we’ve examined their core operations, diverse use-cases, inherent risks, and evolving trends. While these marketplaces continue to serve legitimate purposes, such as enabling secure communication and privacy protection, they also remain hotspots for illicit activities and cybercrime. Dark-web marketplaces operate through encrypted networks, primarily utilizing anonymity-enhancing technologies such as Tor (The Onion Router) and I2P (Invisible Internet Project). Alright, let’s get into the meat of it—the darknet markets that are ruling 2025.
It should force us to think about where harm is really happening online and whether current strategies are looking in the wrong direction. This ability of dark web communities to thrive in disruptions reflects how dark web market users have become experts at adapting to risks, managing disruptions and rebuilding quickly. Despite recent legislative attempts to improve victim support and protection, there has been little success in this area.
- Here are some of the now-defunct dark web markets that were notorious for cybercrime.
- Fresh Tools Market has become a go-to platform for cybercriminals seeking access to malicious software such as keyloggers, Remote Access Trojans (RATs), and ransomware-as-a-service.
- They’re hinting at going decentralized in 2025—less downtime, more trust, right in line with the decentralized trend.
- I do not condone the use of DNMs to purchase or sell drugs and other illegal materials online.
In the first arc of the anime series Lupin the 3rd Part V, Lupin III steals digital currency from the “Marco Polo” darknet market. For a local machine configuration, he recommends a computer purchased for cash running Linux, using a local Tor transparent proxy. By leveraging automated dark web monitoring, organizations can mitigate risks, and take preventive measures before the leaked data is exploited. This platform has rapidly become a key player in the fraud market, trading in PII and SSH credentials while making use of both the clear and dark web. The market emphasizes anonymity and security, conducting transactions exclusively through cryptocurrencies like Bitcoin and Monero. The marketplace requires merchants to pay fees to sell their products, helping ensure a certain level of quality control.
Layer a VPN (e.g., NordVPN) to mask your IP before entering darknet markets. A timeline of darknet marketplace evolution, from Silk Road to 2025’s top players. Compared to its predecessors, Archetyp enforced enhanced security expectations from its users. These included an advanced encryption program known as “Pretty Good Privacy” and a cryptocurrency called Monero. Unlike Bitcoin, which records every payment on a public ledger, Monero conceals all transaction details by default, which makes them nearly impossible to trace. The durability of these markets tells us that if policing responses keep following the same playbook, they will keep getting the same results.
These hackers don’t hide in the shadows as much as you might think. Anything from planting malware and stealing sensitive files to hijacking email accounts or breaking into social media profiles. It’s also a marketplace for digital mercenaries; you’ll find everything from solo hackers offering their skills to well-organized groups that take on more complex or high-stakes projects. Some even have connections to criminal organizations and, in more serious cases, government-backed operations.
Which Wallet Best For Darknet Market
Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net. Despite using a VPN, there’s always a risk of the VPN leaking your IP address through DNS or WebRTC leaks or misconfigurations when on a dark web forum or marketplace. Therefore, you must run an IP leak test to ensure that the VPN is working completely fine and is not risking your digital security.



