Create new handles or pseudonyms to protect your identity throughout your online engagements. By the late 2010s, a myriad of platforms allowed users not just illegal goods but also forums for activism, whistleblowing, and even genuine speech that found little outlet in conventional media. As these marketplaces flourished, they drew the interest of law enforcement. Silk Road’s takedown in 2013 fueled both fear and fascination, marking a high-profile enforcement milestone. However, it didn’t close the chapter on the dark web but, instead, opened the gates for many imitation sites. The subsequent captures of dark web operators resulted in a constant cat-and-mouse game, further embedding the idea of lifestyle communities within the web’s shadows.
How To Access The Dark Web (A Step-by-Step Guide)
It also explores the brains behind the crime rings and their operations, including how they evade detection and how their activities impact individuals and organizations globally. It discusses how dark web users anonymously engage one another on topics such as social issues, politics, and more to avoid the gaze of authoritarian regimes. The author highlights the benefits of the dark web to society regarding the right to privacy and freedom of speech in a world where these values are quickly eroding. Furthermore, Forsay makes the case for data privacy, revealing how big tech such as Google harvests your data without your knowledge. The book notes that the dark web can help you control your privacy without big tech snooping around your online history.
However, with the right knowledge and guidance, you can safely explore what lies in the hidden corners of the Internet. This beginner’s guide will equip you with the necessary information to explore the dark web with confidence and security. And, of course, think twice before sharing too much personal details online. Even the smallest details about you can be useful to cybercriminals. That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web. They’re tightening security and carefully screening anyone who wants to join.
Other Collection Links:
- It means unless you use a VPN that encrypts your internet traffic, they always receive all information about you and your digital life.
- However, some of these alleged services, such as professional ‘hitmen,’ may be scams designed to defraud willing customers.
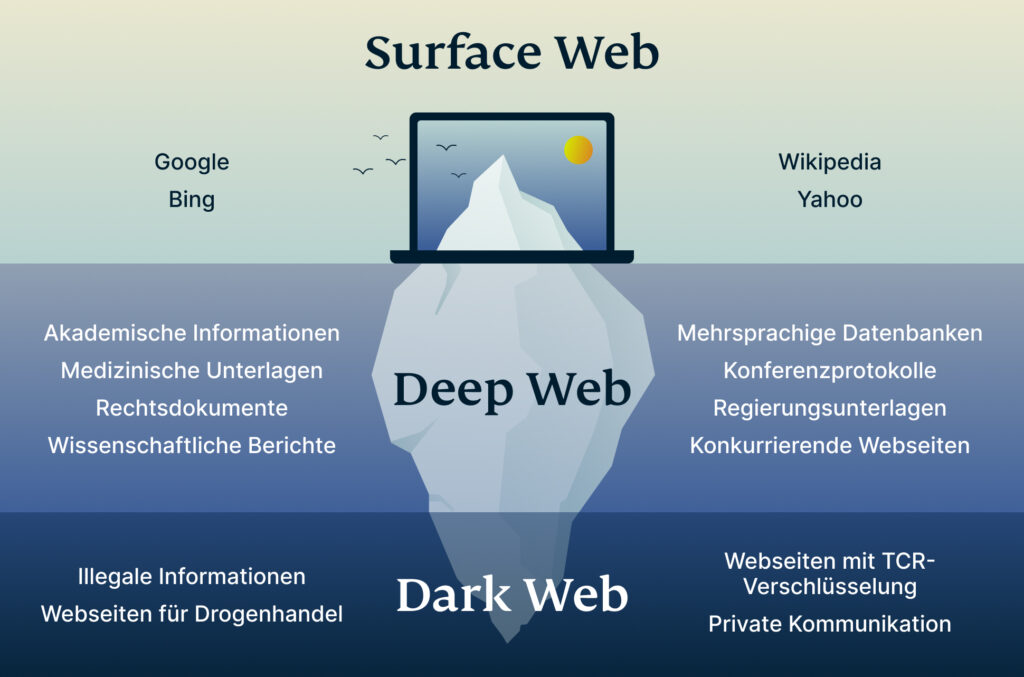
- The Darknet is often utilized for secure communication, discreet information or file sharing, anonymous research without identity exposure, and occasionally for engaging in illicit activities.
- This ensures that your real IP address is hidden from the first Tor relay (it sees the IP address that your VPN provider supplies).
- Each wave of takedowns disrupted marketplaces but also pushed criminals toward more resilient, decentralized models.
In this article, we’re going to explore a hand-picked list of the 18 books that deliver unique, helpful, and thought-provoking insights into the dark web. Dark web books aren’t just how-to guides for breaking the law or dodging surveillance. (Forget what you think you know.) Instead, they offer a peek into the minds of the people who actually navigate this hidden digital realm and explore the real-world impact it has on our society.

Enter A Darknet Web Address
Cybercriminals lurk in the dark web to methodically coordinate their attacks, sell illicit goods, distribute malware and phishing kits, and share other prebuilt exploits. Go behind enemy lines to identify threat actors and their intentions at the earliest stages so you can properly prepare your defenses. These days, it can seem increasingly difficult to protect valuable assets and data from the reaches of threat actors.
Archetyp Darknet Market
DuckDuckGo is the default search engine inside the Tor browser, and once you turn on the Onionize toggle switch in the search box, you’re able to use it to find dark web links. These typically come with “.onion” after them, rather than something like “.com” as on the standard web. Open up Tor, and you won’t suddenly see the dark web staring back at you.
You might want to hide your Tor Browser download using a VPN and your existing browser’s private/incognito mode. Our rigorous research and testing have revealed revealing truths and busted myths. We’ll navigate this intricate maze with you, uncovering its secrets while ensuring your online safety.
Digital Rights And Advocacy Groups
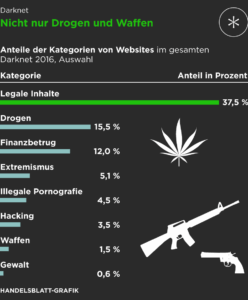
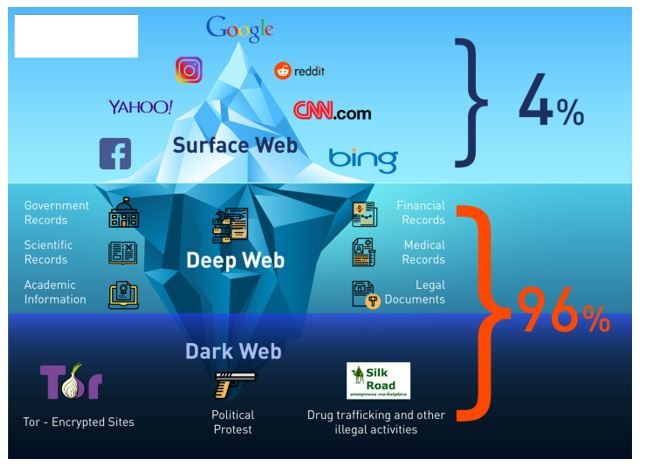
These days, it lists over 11,600 illegal items, including hard drugs, hacking tools, and all kinds of cybercrime services. It also runs on the Tor network, which helps keep things anonymous. The dark web is a hidden section of the internet that you cannot reach with common search engines like Bing or Google. The only way in is through the use of special software that renders all users anonymous and untraceable. Unlike regular e-commerce sites, markets on the dark web often deal with illegal or highly restricted goods and services, such as fake documents, hard drugs, and hacking services.
Why Are All The Darknet Markets Down
Journalists and whistleblowers, including Edward Snowden himself, often use the dark web and Tor to exchange sensitive information. For instance, the Ashley Madison data dump was posted to a site only accessible to Tor users. By hardening your setup, practicing smart behavior and maintaining financial discretion, you can reduce your exposure to common risks. Staying anonymous requires continuous learning, self-awareness and legal caution.

Security Audit Report
In summary, the Tor Browser is your gateway to the darknet, providing a secure and anonymous way to explore and access resources that are otherwise hidden from the standard internet user. Whether for research, social interaction, or simply the allure of the undiscovered, understanding and utilizing the Tor Browser is crucial for anyone looking to venture into this obscure online realm. The Tor Browser is a unique web browser designed specifically to provide users with privacy and anonymity online. By understanding the hazards you may face in the Dark Web and implementing the precautions outlined above, you’ll be better equipped to minimize your exposure to scams, malware, and identity risks. Remember that good judgment, ongoing education, and constant vigilance are your most powerful tools for maintaining a safe and private Dark Web experience.
Tor Browser Über Die Offizielle Website Downloaden

These sites often look basic or outdated, and their URLs are lengthy strings of random letters and numbers. Keep in mind that visiting the dark web isn’t illegal, but engaging in criminal activity there is. Many people go to the dark web to buy things they can’t find elsewhere, but what if what you’re buying is also trying to harm you? Scammers on darknet markets claim to offer legit tools or services, but instead provide you with malicious software that can infect your device. Many people use Tor to avoid surveillance by government agencies, ISPs, or other entities monitoring online activities.
This group consists of a populace whose actions on the internet would rapidly lead to imprisonment or fines. Cybercriminal groups like DDOS have carried out over 140 cyberattacks on companies since Bitcoin’s emergence in 2014. The attacks have led to the formation of other cybercriminal groups and Cyber Extortion. According to recent research, Bitcoin tumblers are increasingly used for money laundering.
Don’t log into any real accounts, reuse usernames, or enter any personal details. Treat every site as untrusted unless you’ve verified it from multiple sources. You’ve probably heard that Tor makes you anonymous on the dark web — but that’s only half true. If you don’t use the right tools or settings, your ISP can still flag your connection. And once you’re inside, one wrong click on a fake .onion site can expose your identity or infect your device with malware.