It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. It has a proprietary onion site in the Tor network to give you safe access even if your country restricts VPN usage. The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers. NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites. It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe.
We are a Tor network dark web directory listing created in order to monitor and study popular darknet marketplaces and onion services. Similarly, threat intelligence is another tool that involves the collection and analysis of data about potential or existing cyber threats to help organizations understand and prepare for future risks. This can include gathering information from various sources, including dark web forums, and analyzing trends related to cybercrime. Finally, there is always the risk that the credit card information being sold on darknet carding sites is fake or outdated.
- Carding forums act as central hubs for cyber criminal activity—particularly for promoting websites and Telegram channels that sell stolen credit card data.
- (b) is the deep web, which consists of sites that require a login to access like email accounts, banking portals, and subscription services.
- Because of its anonymity, the dark web is filled with illegal services and is used by numerous criminal groups, including ransomware gangs.
- I recommend bookmarking verified links rather than relying on search results.
Buyers may spend money on credit card information that is not valid, which can result in financial loss and frustration. Stolen credit cards are often used to make purchases at specific sites that don’t have protections against fraud. Card Shops typically host the trade of credit cards and other stolen financial information, making it easy for cybercriminals to find what they’re looking for. Free and paid tutorials on the dark web teach fledgling criminals how to use stolen credit cards. A dark web carding market named ‘BidenCash’ has released a massive dump of 1,221,551 credit cards to promote their marketplace, allowing anyone to download them for free to conduct financial fraud. Users typically seek to either buy stolen credit card information for fraudulent activities or sell stolen data to profit from criminal endeavors.
How To Find New, Active Dark Web Links
That merchant specifically mentioned that using a stolen card on a store that uses Verified by Visa (VBV) will likely void the card. Verified by Visa is a service that prompts the cardholder for a one-time password whenever their card is used at participating stores. Comparitech researchers sifted through several illicit marketplaces on the dark web to find out how much our private information is worth.
Banks Cratering Because Of Poor Risk Management
For example, you can find information unavailable to the public and share data privately while protecting your online identity. Note that most dark web transactions are carried out using Bitcoin or other cryptocurrencies. In 2025, darknet markets continue to provide a secure and efficient platform for the trade of pharmaceuticals and digital products. These platforms leverage advanced encryption technologies and decentralized systems to ensure user privacy and transaction security. The integration of cryptocurrencies like Bitcoin and Monero has further enhanced the reliability of these markets, offering users a seamless and anonymous payment method. These stolen cards have value because they can be used to purchase expensive items or gift cards, which can then be resold for cash. mark it means it has been verified as a scam service and it should be avoided.|Recovering stolen data is highly challenging, but contacting financial institutions immediately can help mitigate potential losses. Accessing the darknet typically requires special software like Tor, which anonymizes user activity. Fraud-related products, consumer electronicselectronics, self-defense products, and even hosting. If you browse the dark web using the Tor Browser, your IP address will be hidden from the sites you visit. When you use Tor, your traffic is routed through multiple relays (or servers).|Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. While the anonymity of cryptocurrencies makes it difficult, law enforcement agencies have ways to track illegal activity through advanced forensic techniques.|The dark web contains numerous security risks, from malware to scams and illegal content. Thankfully, there are effective measures that keep you secure on the dark web and ensure you remain protected and anonymous while accessing .onion sites. The threat actor’s marketing strategy involves leaking a large number of credit cards to attract potential clients from hacking and cybercrime forums. This move is likely to increase the platform’s popularity and draw in new customers.}
Curious About How Breachsense Can Help Your Organization Detect Credit Card Fraud? Book A Demo To Learn More

Deep web websites have to be hosted somewhere, and Impreza Hosting is one of those anonymous dark web hosting services. A host is basically a website’s house, or where it lives and takes up space. Impreza provides an affordable hidden space for black websites to base their operations. Impreza rents servers, registers domains, and hosts email similar to sites like GoDaddy. Sci-Hub provides free access to scientific papers, with millions of documents. Scientific journals often put their articles behind a paywall and charge high fees for access, but Sci-Hub offers open access to read or download research papers.

Features Of Dark Web Carding Forums
According to the seizure notice, SSNDOB has processed over $19 million worth of sales using cryptoassets. Unlike regular deep web sites such as your email account, the dark web is inaccessible unless you have special tools or software like the Tor browser. Some even say that the real dark web requires an invitation to participate. The BBC and other well-known news services are blocked in some parts of the world.
The stolen credit card information is usually obtained through phishing scams, malware attacks, or data breaches. Carding sites are hidden on the dark web, accessible only through specific software, such as Tor. These sites provide an anonymous platform for carders to advertise, buy, and sell stolen credit card information, along with tools and tutorials for committing carding fraud. Card fraud is no longer just a consumer issue; it could be a deadly threat to online businesses. One of the most concerning forms of cybercrime is carding, a scheme fueled by stolen credit card data and perpetuated through the dark web.
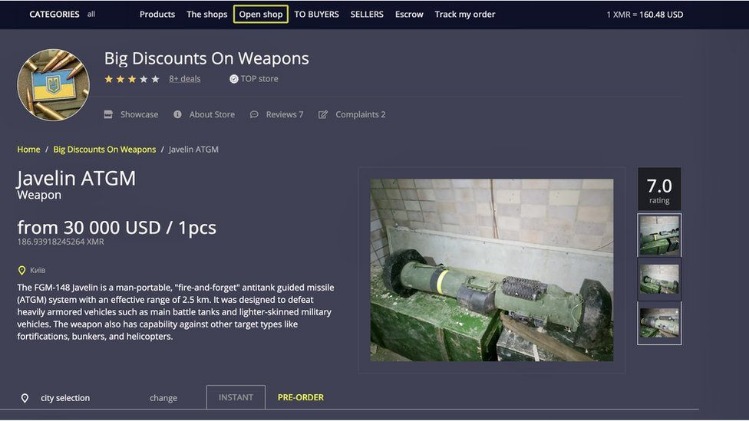
Some vendors include access to a SOCKS5 internet proxy to help buyers avoid being blacklisted. Thieves often buy cards to use on specific sites that don’t have security features like Verified by Visa (VBV) or MasterCard’s SecureCode. These cards can be used to make purchases online or in-store, and can even be used to withdraw cash from ATMs.
“No Place In Our Networks”: FCC Hangs Up On Thousands Of Voice Operators In Robocall War
Facebook is aware of attempts by many governments to restrict access to a tool that allows strangers across the web to talk and collaborate freely. While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored. Your real information could be exposed at these nodes, allowing third parties to intercept your dark web activity. That’s why we recommend connecting to VPN before accessing Tor—VPN encryption protects your data, and changing your IP adds an extra layer of privacy to protect you. Do note that we haven’t verified the legitimacy of the provided information, or the vendors on these darknet forums. As a result, it’s totally possible for some of these forums or vendors on these forums to be complete scams.
The Dark Web’s Largest Forum For Stolen Credit Card Data Is Shutting Down
We review and list tools and products without bias, regardless of potential commissions. Sign up for our newsletter and learn how to protect your computer from threats. Voluntary retirement, or “sunsetting”, is second to “exit scam”, which is where the market admins pull the rug from under their clients and partners and run away with the money. If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. Just Another Library is one such service, with a wealth of books covering computer programming, science, and niche hobbies (sailors’ knots, anyone?).
They provide a comprehensive network of medical services for residents, including cancer, emergency, hospice, pediatrics, and urgent care. Nowadays, digital transactions and virtual interactions aren’t exactly optional. People can’t keep their information off the web due to professional reasons, and many processes are exponentially more convenient through an online profile.
- Inform your bank or credit card issuer immediately to freeze your accounts and prevent further unauthorized transactions.
- This is high-level protection; no one can intercept your data or activities.
- The dark web’s anonymity accommodates illegal activity and contributes to its reputation as being a haven for criminals.
- The resulting financial loss from stolen information is tremendous, not only for the individual victim but also for the financial provider and any involved organizations.
- Voluntary retirement, or “sunsetting”, is second to “exit scam”, which is where the market admins pull the rug from under their clients and partners and run away with the money.
Top 10 Deep Web And Dark Web Forums
It aims to expose abuses of power and betrayal of public trust through investigative journalism. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. While this wave of sunsetting may sound like great news to a lot of us, law enforcement have mixed feelings about it. The underground market accepts cryptocurrency payments of Bitcoin, Litecoin, Ether, and Dash.
Carding is the act of using stolen credit card information to make unauthorized purchases. The sheer quantity of data available for purchase has created a bulk sales mentality for Dark Web customers. Fake keypads are sometimes placed over the legitimate ones to record your PIN.