
The 2013 Yahoo data breach is a classic case of how security flaws and weak encryption can expose your business to cyber threats. Continuous Authorization is a security concept ensuring ongoing validation of users’ access rights within a system. On February 21, 2024, United Healthcare was hacked in a ransomware data breach that impacted its Change Healthcare (CHC) unit. In today’s digital age, many individuals and organizations rely on technology for communication, transactions, and data storage. Separation of duties (SoD) is the division of tasks among organization members to prevent abuse, fraud, or security breaches. Hackers accessed thousands of PayPal user accounts between Dec. 6 and Dec. 8, 2022.
Inconsistent Customer Support
By following best practices for online security, you can help safeguard your hard-earned money from cybercriminals. While Cash App is a popular and convenient payment platform, it is not immune to cyber threats. Users should take precautions to protect their accounts from hacks and scams. Sending and receiving money is free, just like standard deposits to your bank account, and takes 1-3 business days to arrive. If you think Cash App is taking money without permission for service charges, keep in mind that they charge 0.5% to 1.75% for instant deposits. In theory, you should put it to use to make despite your friends afterdividing taxi fare or to refund 50 percent to an own sister because they paidto your Mother’s Day gift in full.
Cash App does not require users to send money for any reason, and it’s not possible to claim cash prizes on Cash App by sending money. The Cash App team does give away free money, Bitcoin, or stocks on “Cash App Fridays” via social media platforms like Instagram and Twitter. All you have to do is reply with your Cash App “$cashtag” for a chance to win. Not only did he lose his “investment” — but the scammers also took over Thompson’s Facebook account and scammed his close friends and relatives out of thousands of dollars. Cash flipping refers to scammers offering to “flip” your money with a promise of guaranteed higher returns.

Sending Group Texts On Pixel 6: The Definitive Guide
Most cash applications don’t offer buyer protection and will do very little to get you a refund. Cash App is a digital payment platform that allows users to send and receive money quickly and securely using their mobile devices. Frequently review your cash app account activity to identify any unauthorized transactions promptly. Report any suspicious activity to the cash app’s customer support and consider freezing your account temporarily until the issue is resolved. Engaging in activities that exploit system vulnerabilities can violate terms of service, breach laws, and lead to legal penalties. Furthermore, there are risks of account suspension or termination, financial losses, reputation damage, and unauthorized access.
Which Darknet Market Are Still Up
You can also get a Cash Card that’s linked to your Cash App account balance. Instead of using your phone, you can use the Cash Card anywhere Visa is accepted. First, Starks contacted Cash App via email, but they needed time to investigate the transaction. So, in a rush to receive his money, he Googled “Cash App support” and was taken to a legitimate looking website, complete with the Cash App logo. Jory MacKay is a writer and award-winning editor with over a decade of experience for online and print publications.
Scammers message you claiming huge returns if you invest a small amount of cryptocurrency, but you’ll never see any returns. Crypto scammers also use hacked social media accounts to launch Cash App scams to the hacked account’s friend list, hoping to cash in before anyone notices. Cash App is a widely used mobile payment service that allows users to send and receive money, invest in stocks, and even buy cryptocurrency. Its convenient features make it a popular choice for many, but they also attract malicious actors looking to exploit vulnerabilities. If you think your phone has been hacked, the first thing to do is disconnect it from the internet and run an anti-malware scan.
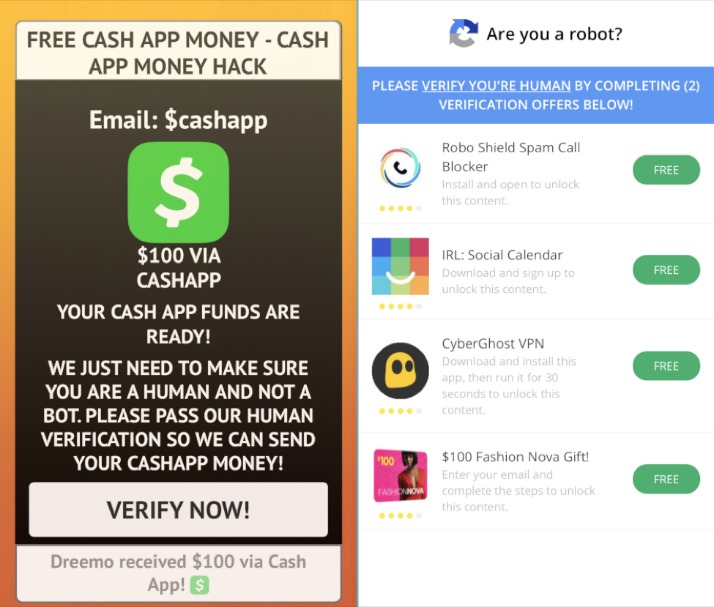
Are There Any Legitimate Cash App Money Generators?
This referral bonus pays you $5 on Cash App when one of your friends or family uses your invite code and sends $5 or more from their new Cash app account. The victim is given detailed instructions to send the items or send photos of the back and front of the cards. This gives the funds back to the fraudsters before the check is returned as fictitious. Welltok is a communications platform that allows patients and physicians to speak while encouraging healthy lifestyles. We reported on Mr. Cooper—one of the nation’s largest mortgage providers—a month ago.

They also found a wallet with bitcoin from the original hack of Silk Road in 2012. Segregation of Duties (SoD) is a risk management principle that ensures critical tasks are divided among different individuals to prevent conflicts of… Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft that allows users to remotely… Fine-grain access controls are a type of access control that enables granular access to systems, applications, and data. Continuous monitoring is a systematic and ongoing process that uses automated tools and technologies to monitor the…
What Should I Do If I Suspect My Account Has Been Compromised?
It’s easier than ever to score free money these days since plenty of apps and programs have bonuses up for grabs. In fact, there are numerous Cash App hacks you can use to maximize your earnings and make some quick money. Ignore any online posts where people offer services that aren’t available yet and request payment through Cash App.

How Do I Know If My Cash App Account Has Been Hacked?
OAuth (OAuth 2.0 since 2013) is an authentication standard that allows a resource owner logged-in to one system to delegate limited access to protected… NIST compliance broadly means adhering to the NIST security standards and best practices set forth by the government agency for the protection of data… A man-in-the-middle (MITM) attack is a cyber attack in which a threat actor puts themselves in the middle of two parties, typically a user and an… Log analysis is the practice of examining event logs in order to investigate bugs, security risks, or other issues. Lateral movement is when an attacker gains initial access to one part of a network and then attempts to move deeper into the rest of the network —…
The Concept Of A Dark Web Cash App Hack
An application gateway is a security measure that protects web applications. Anomaly detection is the process of analyzing company data to find data points that don’t align with a company’s standard data… Agentless monitoring is a form of IT monitoring that does not require the installation of a software agent. Active Directory Bridging is a technology in the field of networking that aims to enhance the communication… Access control lists (ACL) control or restrict the flow of traffic through a digital environment. Terminations, even rightful ones, leave a bad taste in the recipient’s mouth — in some cases, so much so that the former employee decides to go on a revenge mission.
Despite being a common part of our daily lives, ATMs are vulnerable to exploitation by even the least skilled attackers. The business will also likely suffer a revenue decline, yet the company’s app is too ubiquitous to fall out of favor with the masses. Unlike your bank account, money sent via Cash App (or other mobile payment apps such as Zelle and Venmo) isn’t FDIC insured.
- It must be noted that Cash App’s threat detection measures are elite, yet there is only so much a business can do to prevent internal data theft.
- NoSQL Injection is a type of injection attack that exploits vulnerabilities in NoSQL databases by injecting malicious code into…
- Additionally, if you unknowingly gain unauthorized access to someone else’s funds through the glitch, you could face criminal charges.
- Recently, reports have emerged regarding Cash App accounts being compromised by hackers operating in the dark web.
- Data Security Posture Management (DSPM) refers to the proactive and continuous assessment, monitoring, and enhancement of an organization’s data security…
Additionally, to set up a Cash App account, you need to provide some personal and financial information, including your phone number, email address, and bank account information. If you notice phone hacking signs, stop using Cash App and any other payment app immediately. Though Cash App itself is safe, the quick access to money has opened the platform to a variety of different types of scams.
When you initiate a transfer, your information is encrypted, and you’re secured by Cash App’s vulnerability management suite that protects you from scammers. The member of the ShinyHunters hacker group Sebastien Raoult was sentenced in U.S. District Court in Seattle to three years in prison and more than $5 million in restitution for conspiracy to commit wire fraud and aggravated identity theft. Hidden beneath the surface of the internet lies the dark web, a parallel online universe inaccessible to regular search engines. It has gained notoriety due to its association with illegal activities, including drug trafficking, identity theft, and even hacking.



