Therefore, our process for locating advertisements starts with selecting recent BG sites. We, therefore, use the following 4-step process to reduce the DWM dataset to a list of Bitcoin addresses where a “mining fee” can be deposited as intended by the owner of a BG site. Figure 3 presents a screenshot depicting the status of three cloned “Swedish Bitcoin Multiplier” sites as of November 20, 2024. The first site has been running on a rented server since January 29, 2024 (as shown in the “Discovered at” column).

Which Darknet Markets Accept Zcash
Scamsearch is a tool that searches public databases to identify wallet addresses, usernames, or websites connected to fraudulent activities. Investigators can quickly determine whether a cryptocurrency address has been flagged for scams, providing an essential starting point for further analysis. The advancement of the internet has ushered in a multitude of innovations and prospects. Yet, alongside the surface web exists a concealed domain known as the Dark Web, notorious for fostering illicit activities. Cryptocurrencies, notably Bitcoin, play a pivotal role in facilitating transactions within this covert network.
The Evolution And Resilience Of Dark Web Marketplaces
While it might appear tempting to venture into the dark web, it’s crucial to understand that the risks here are far more severe compared to the deep web. As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web. And most importantly, be patient as you’ve to sort through a lot of useless results. These search engines work best if you already know what site you’re looking for, not for general browsing. Hence, you never know when a popular .onion site is going to vanish, or even die.
The Threats Posed By Dark Web Bitcoin Mixers
Despite these advancements, criminals continuously adapt, utilizing privacy coins and decentralized networks to evade detection. Challenges like cross-border enforcement and privacy concerns complicate regulation. To outpace criminals, continuous innovation in AI-driven analytics and forensic tools is necessary, ensuring real-time monitoring and intervention. Blockchain forensics and artificial intelligence have advanced crypto crime detection by trawling humongous databases in order to flag suspicious transactions.
Global Korea: South Korea Should Double Down On A Global Role In The Era Of Trump

Thankfully (at least for this specific purpose), the blockchains that power cryptocurrencies are largely transparent, and companies like Chainalysis, CipherTrace and Crystal Blockchain provide blockchain forensics services. Efforts are being made to address these concerns and distinguish legitimate uses of bitcoin from its association with the dark web. Regulatory measures and increased transparency are being implemented to ensure that bitcoin transactions are conducted legally and responsibly. In addition to scams, the dark web is also teeming with other fraudulent activities related to Bitcoin. Some individuals may offer to sell Bitcoin at below-market rates, only to disappear after receiving the payment.

Data Leak Checker: Has Your Email Been Hacked?
And while these are critically important types of crime to pay attention to, we are going to zoom in specifically on dark web marketplaces. On one hand, increased regulation and scrutiny may deter individuals from engaging in illegal activities, ultimately making the dark web a safer place. On the other hand, it may drive criminals to explore alternative options that offer better privacy and security. This could lead to the emergence of a new underground economy built around these privacy-focused cryptocurrencies. Cryptocurrency exchanges are online platforms where individuals can buy, sell, and trade various cryptocurrencies. These exchanges provide the necessary infrastructure for converting digital currencies into fiat currencies and vice versa.
A chart from Meiklejohn’s paper showing her “clustering” of Bitcoin addresses for early cryptocurrency entities. The hundreds of addresses Meiklejohn identified and tagged manually with those 344 transactions represented only the tiniest fraction of the overall bitcoin landscape. But when she combined her address tagging with her chaining and clustering techniques, many of those tags suddenly identified not just a single address but an enormous cluster belonging to the same owner. With just a few hundred tags, she had put an identity to more than a million of Bitcoin’s once-pseudonymous addresses. Considering Bitcoin’s mechanics for the first time, Meiklejohn was intrigued.
Updated Search Terms From Badawi Et Al

This is because a Tor websitedemonstrates a (sometimes symbolic) commitment to privacy. The New York Times and the CIA, for example, are both hoping tofacilitate communication with virtual walk-ins who can provide sensitiveinformation. The connection between bitcoins and the dark web exemplifies a complex interplay of anonymity and illicit activities.
Onion links have no regular domain names registered under the domain name registry. Instead, they are designed using a cryptographic key and can be accessed only through software like the Tor browser. One option is to try DuckDuckGo’s .onion version, which is great for privacy. Other options include Ahmia and NotEvil, which focus on listing .onion links.
Cryptocurrency has transformed the landscape of digital transactions, offering a new layer of anonymity that traditional financial systems cannot match. Bitcoin was among the first to gain traction in these underground markets, paving the way for an array of altcoins designed specifically for privacy.The rise of blockchain technology further enhances this appeal. It provides secure and transparent transaction records while maintaining user anonymity. The Dark Web is a part of the internet that isn’t indexed by traditional search engines.
The Rise Of Crypto Fraud
- Unlike traditional payment methods, such as credit cards or bank transfers, bitcoin transactions are not directly linked to personal identities.
- Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
- Law enforcement agencies around the world actively monitor the Dark Web for illegal activities, and many criminals have been caught and prosecuted as a result of their actions online.
- Programs with the fitting intermediary can arrive at these sites, however, others can’t.
- After manual removal, 832 dark web BG sites remained, meaning that 0.04% of the dark web, according to our analysis, consists of BG sites.
The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. Whether local or international goods, research documents, banned drugs, you name it, everything is available on this dark web platform (that’s one of the reasons why this should be monitored for security purposes). You will find all the necessary .onion links to access any content or service on the dark web.
One of the most persistent myths surrounding Bitcoin is that it is exclusively used for illegal activities on the dark web. While the dark web only represents a small fraction of the internet, it has become a haven for criminal activity. However, it’s important to note that not all activity on the dark web is illegal, and many people use it for legitimate purposes such as anonymous communication and accessing censored information. The clear and dark web offers different advantages and challenges when running scam websites. The clear web offers broad reach and easy access but with higher levels of control.

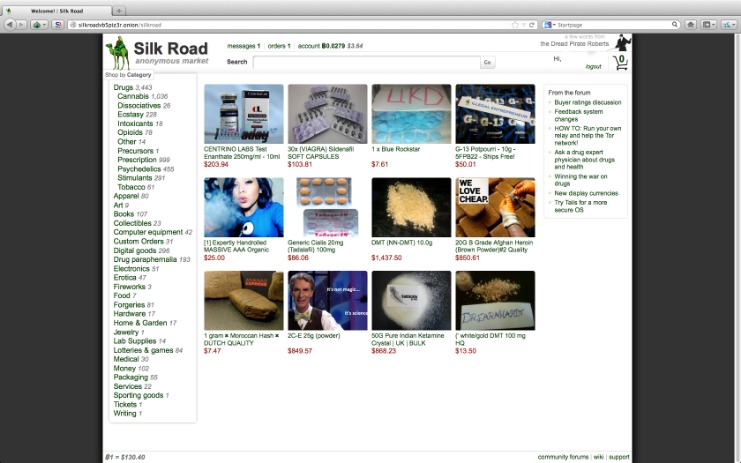
When Meiklejohn first heard about Bitcoin in 2011, she had started her PhD studies at UCSD but was spending the summer as a researcher at Microsoft. A friend at the University of Washington had mentioned to her that there was a new digital payment system that people were using to buy drugs on sites like the Silk Road. So, with heads-down focus, she filed Bitcoin’s existence away in her brain, barely considering it again for the next year. One of the most dangerous aspects of the Dark Web is its potential to facilitate large-scale cyberattacks. Hackers can purchase everything from stolen data to zero-day vulnerabilities (security flaws in software) that allow them to exploit systems before the vulnerabilities are patched. Thus, regardless of which of the pair you intend to use, you should start by buying bitcoin.
This change persists until the end of the observed period of the data set (also see Supplementary Information S4). In contrast to the other types of sellers, the median income of U2U-only sellers increases after operation Bayonet. Moreover, we observe a trend of increase in their median income relative to the value before operation Bayonet—an increase of almost six times by the end of the period of observation (see Supplementary Information S4). Further supporting this interpretation, we observe that the trading volume of the U2U network increases after Bayonet, while the trading volume of markets decreases (see Supplementary Information Section S4). The role of Bitcoin in the dark web transactions is a complex issue that requires a nuanced understanding.
The increased use of Bitcoin in the dark web has raised concerns for regulatory bodies and governments around the world. The anonymity of Bitcoin transactions has made it difficult to monitor and regulate its use, leading to potential criminal activities. However, some argue that Bitcoin can also be used for legitimate purposes and that a blanket ban on its use is not the solution. Despite these common misconceptions, the digital asset terrain is increasingly being regulated and the chances of getting away with the illegal use of cryptocurrencies are getting slimmer by the day. So next time you want to make an illegal purchase using cryptocurrency on the dark net, you might want to think again.