
Additionally, a scarcely observed “Latest Orders” segment is featured in the lower left panel of the primary market screen, which exhibits the most recent purchases made by buyers on the market. Due to its relatively diminutive size, Cypher has waived the vendor bond for vendors who have conducted over 200 sales on other markets. Although the market has yet to gain as much momentum as its competitors, it exhibits no indications of deceleration. The Cypher Market, a relatively small darknet market, has been in operation for over three years, yet has not garnered significant recognition from the broader community. Although the range of products and vendors is restricted, the market does offer sufficient vendors to cater to the primary markets worldwide, namely North America, the European Union, and Australia. Beware that every time this issue happens, indeed no decryption occurs.You can see this with debugging, for some reason the encrypted messageis passed as the result in the decryptor despite the private key beinglarger than 2.

Dark Matter Market
Successfully completing Cypher challenges can significantly boost your confidence and problem-solving abilities in the field of cybersecurity, making you a more proficient and versatile ethical hacker. Embrace the opportunity to sharpen your cryptography skills and dive into the intriguing world of Cypher challenges. Simple code translation tools are primarily designed for entertainment and basic privacy, not securing sensitive data. While they can obscure messages from casual observers, they don’t provide the level of encryption needed for truly confidential information.
OnionLand Search
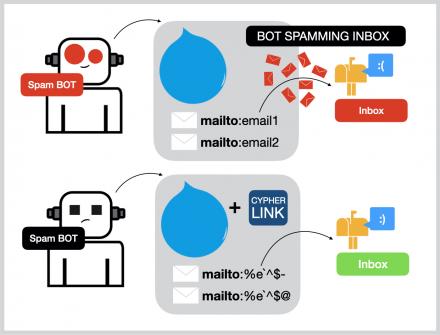
CipherLink is a lightweight, high-performance communication library designed to provide end-to-end encryption for secure data exchange between clients and servers. Leveraging industry-standard AES-GCM encryption, CipherLink ensures the confidentiality and integrity of messages transmitted over the network. See both encoded and decoded versions simultaneously for quick verification and adjustments. One advantageous aspect of Cypher is its notably uncomplicated registration procedure, which solely necessitates the establishment of a username and password. The captchas employed by the platform are among the most straightforward, and the loading times of its pages are among the swiftest.
- Explore online platforms like HackTheBox forums, Reddit’s hacking communities, and cybersecurity blogs for a wealth of resources on tackling challenges similar to Cypher.
- If randomly choosen,private key generation takes a lot of time, therefore the default is true.
- Understanding the target’s infrastructure through thorough reconnaissance lays a solid foundation for successful penetration testing.
- The any() function returns true if the predicate holds for at least one element in the given LIST.
Under Actions to the right of the Cypher statement is a pencil icon. Click on the pencil to launch the appropriate editing tool for the Cypher statement. A query marked as Visual will launch Cypher Builder, otherwise the Cypher Suite is launched. A Canadian market established in 2021, WTN offers over 9,000 products, including narcotics, fake goods, and digital services.
Identifying Target Services And Ports
The date.transaction() function returns the current DATE instant using the transaction clock. The date.statement() function returns the current DATE instant using the statement clock. The date.realtime() function returns the current DATE instant using the realtime clock.
The time.truncate() function truncates the given temporal value to a ZONED TIME instant using the specified unit. Map projection with an all-map projection to project all key-value pairs from a MAP without explicitly listing them. Property values can be accessed dynamically by using the subscript operator . A subset check using the all() function verifies if all elements of one LIST exist in another. CALL subqueries can execute batches in parallel by appending IN n CONCURRENT TRANSACTIONS, where n is an optional concurrency value used to set the maximum number of transactions that can be executed in parallel. Multiple UNWIND clauses can be chained to unwind nested list elements.
Embrace The Future Of Cypher Url With Our Innovative Platform
Its intuitive design promotes exploration, yet users are advised to navigate with caution and a sense of moral responsibility given the darknet’s nature. Cypher beckons those in pursuit of a novel and evolving adventure into the deeper echelons of the digital realm. The platform is in a phase of development, with its management team focused on rolling out significant improvements to enhance the user experience. Cypher Market has swiftly emerged as a significant entity within the darknet’s commercial landscape, acclaimed for its clean, minimalist aesthetic that places a high emphasis on user experience.

It’s incredibly versatile with multiple cipher options, and I love how quickly I can switch between encoding and decoding. The Secret Code Translator has been a game-changer for my cryptography lessons! My students love experimenting with different ciphers, and it helps them understand encryption concepts in a hands-on way.
Market Screenshot
We recommend you check the website using our check list or by contacting the company directly. I was hesitant to try a new cypher market marketplace, but I’m so glad I did. The level of customer service and attention to detail is truly impressive.
Merge Using Node Property Uniqueness Constraints Matches An Existing Node
When immutable is specified in conjunction with a REVOKE command, it will act as a filter and only remove the matching immutable privileges. Deny immutable START privilege to start all databases to the specified role. Unset the home database for the specified user and fallback to the default database. Create a fulltext index on relationships with the name index_name and analyzer english.The other index settings will have their default values. Create a fulltext index on nodes with the name index_name and analyzer swedish.The other index settings will have their default values. Create a range index on relationships with type KNOWS and property since with the name index_name.
Grant CREATE NEW NAME privilege to create new property names on all databases to the specified role. Grant CREATE NEW LABEL privilege to create new labels on all databases to the specified role. Grant SHOW CONSTRAINT privilege to list constraints on a specified database to the specified role. Revoke DELETE privilege on all nodes and relationships in a specified graph from the specified role.

The interface is super intuitive, making it perfect for classroom demonstrations. Seamlessly switch between Caesar, Vigenère, and other popular encryption methods. Create varied levels of message security with different coding algorithms. Real-time security for high-frequency trading and financial markets. Takes in the public key and the message, then encrypts the message.
Music makes life better — but only if it’s coming from a safe, legit source.

The tool also handles special characters and spaces, making it versatile for different coding needs. Some versions even include historical codes like the Pigpen cipher or Morse code. This translator is a lifesaver for creating authentic coded messages in my detective novels. I can quickly generate different types of ciphers that actually work, which adds an extra layer of realism to my stories. Produce complex encrypted messages using keyword-based polyalphabetic substitution for enhanced security.
Cypher Market
The character_length() function returns the number of Unicode characters in a STRING.This function is an alias of the size() function. The char_length() function returns the number of Unicode characters in a STRING.This function is an alias of the size() function. The single() function returns true if the predicate holds for exactly one of the elements in the given LIST. The all() function returns true if the predicate holds for all elements in the given LIST. The relationships() function returns a LIST containing all the RELATIONSHIP values in a PATH. The nodes() function returns a LIST containing all the NODE values in a PATH.



