
The useful site allows you to see how a website looked at an earlier date. This lets you check what information it contained at a previous point in time. The anonymity that onion routing provides slows down your internet considerably. For this reason, anybody who wants to privately stream in HD, play games, torrent, make video calls—or do anything else that requires fast speeds—is advised to use a VPN instead. What you may not know is that you can use Tor browser to access regular HTTPS websites on the surface web. This prevents tracking and fingerprinting, because Tor browser isolates each website you visit, meaning that third-party trackers and ad networks can’t follow you around.
You won’t be able to find The Hidden Wiki using regular browsing methods. Actually, here are more Dark Web sites that Google won’t let you find. If you want to move on to something a little more invisible, you can search for email addresses, criminal records, social media profiles, current and previous addresses, and more.
The Role Of Forest VPN In Dark Web Exploration

The dark web is a small part of the deep web, which consists of all internet content not indexed by traditional search engines like Google. While the deep web includes secure databases and private company sites, the dark web requires special browsers like Tor to access. It offers anonymity, making it a haven for those seeking privacy and freedom from surveillance. Despite its cheeky name, not Evil is a serious contender in the realm of deep web search engines, boasting an impressive index of over 32 million sites and 14 million onion links. As a non-profit endeavor, not Evil distinguishes itself by adhering to strict guidelines, eschewing illegal services and materials, including adult content, narcotics, and firearms markets. Regular search engines like Google and Bing don’t index dark web websites, so you need a dark web search engine to help search these hidden areas of the internet.
What Is The Dark Web? How To Access It And What You’ll Find
That said, most experts agree that at least some nodes on the Tor network have been compromised by intelligence agencies like the CIA and the NSA. This design choice significantly reduces the risk of inadvertently clicking on harmful links or dangerous sites. The Not Evil is relatively safe, as it doesn’t track users; however, it doesn’t filter malicious content, so caution is still needed. Although reported as active, there is limited information on Not Evil’s current status, so availability may vary. The surface web—which we use for searching day-to-day information—is only its tip.
Unlike conventional search engines, not Evil employs a unique ranking system based on user clicks. The more clicks a link receives, the higher it ranks in search results, reflecting its relevance to user queries. This approach compensates for the lack of traditional metrics like PageRank on the Dark Web, where onion sites seldom interlink and maintain short lifespans.
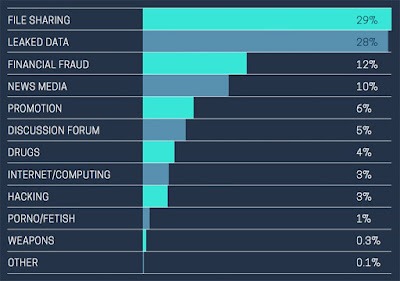
What Percentage Of The Internet Is Dark Web
The dark web presents various threats, including malicious software and computer viruses, posing risks to users’ systems and data security. Users also face the potential danger of government monitoring and surveillance — or scams and fraud, and other activities that can lead to financial loss and identity theft. When accessing the dark web, the first step is to install a dark web-friendly browser on your computer.
Online Best Dark Web Search Engines For Tor Browser

Get in touch with one of our experts to learn more about how our tools can help you gain better access and insights from sites and content far beneath the surface web. The internet is often considered a vast, open space where information is freely available through search engines like Google, Bing, and Yahoo. However, this surface web only represents a small fraction of the internet.
Link11 Highlights Growing Cybersecurity Risks And Introduces Integrated WAAP Platform

Accessing blocked content can result in being placed on a watch list or imprisonment. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It is a component of Whonix, an operating system that functions as a whole inside a virtual computer. It includes all the essential productivity software, including MS Word and an email client.
Understanding The Impact Of Dark Web Search Engines
First and foremost, you want a search engine that is private and secure, as well as one that can be used anonymously. The Tor network consists of a series of volunteer-run servers that route internet traffic through a series of encrypted tunnels. This makes it difficult for anyone to track your online activity or identify your location. It is worth noting that for clearweb, web browsers like Brave and Antidetect browser
- Ahmia and Not Evil are also likely popular among security-conscious users.
- Beneath the surface lies the deep web, a realm of unindexed content, and within it, the dark web.
- Its JavaScript reliance sparked privacy debates, but its ~50,000-site index marked a shift toward user-friendly tools.
- Though you likely won’t remember the addresses of onion websites, you can find these URLs on various websites on the internet.
- Known for its broad index, Haystak offers both free and premium versions.
- Phobos has a very simple user interface that only includes a search bar.
At Startpage.com, they take into account the privacy dangers of recording people’s search behavior, and given their team’s strong convictions about privacy, they decided to act accordingly. A quick guide for developers to automate mergers and acquisitions reports with Python and AI. Learn to fetch data, analyze content, and generate reports automatically.
- Avoid direct engagement; document evidence offline and consult ethical guidelines to prevent backlash.
- The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China.
- Additionally, exercise caution and be aware that the Dark Web contains illegal and dangerous content.
- Tor’s mobile browser, with 20% of users by 2025 (Tor Project metrics), drives demand for responsive, low-bandwidth engines.
- The original (linked below) is still considered the most reliable, so try to avoid counterfeit versions.
Here, we’ll delve into the world of dark web search engines, shedding light on how they work, the best ones to use, and ways to stay safe while exploring this hidden realm. While the dark web has legitimate uses for privacy and information sharing, it also contains illegal activities and potential threats. To navigate it safely, it’s crucial to use a reliable VPN, like Forest VPN, alongside the Tor browser to enhance your security. There are multiple search engines on the dark web that can help you find what you’re looking for. DuckDuckGo’s no-track dark web search service can be accessed in the Tor browser and is an excellent resource for information about the dark web.
This setup ensures anonymity while leveraging NotEvil’s privacy-centric, no-log design. By 2030, ethical debates over content moderation could split the ecosystem, with some engines (e.g., Torch) remaining unfiltered and others (e.g., NotEvil) adopting stricter policies. Users will need to navigate this divide, favoring open-source tools for transparency. NotEvil could integrate differential privacy techniques to share aggregate data, aiding researchers studying dark web trends. This requires balancing utility with anonymity, as even anonymized data risks deanonymization if mishandled.
Keep Tor Browser Updated
I found in my tests that all features work identically to the regular version. His work empowers journalists, researchers, and privacy advocates to safely access unindexed content. Syed’s expertise stems from hands-on testing of tools like Ahmia, NotEvil, and Haystak, coupled with a rigorous commitment to operational security. Directories like Torlinks provide curated, categorized links for quick, structured access to trusted sites, pros including ease for beginners and reduced spam exposure.



