In June 2025, the ShinyHunters group, tracked as UNC6040, compromised one of Google’s corporate Salesforce CRM instances. The breach affected prospective Ads customers, mainly small and medium businesses. Google confirmed there was no impact on Google Ads, Google Cloud, or other product data.
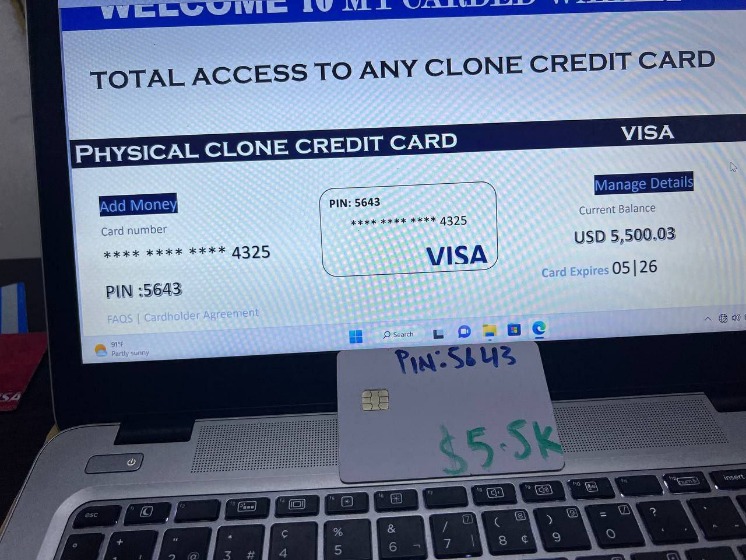
- Pretty much everything you would need to commit credit card fraud or launch phishing attacks against the cardholder.
- A major data breach has exposed the identities of over 100 UK personnel, including MI6 officers and special forces, along with the personal information of nearly 19,000 Afghans who worked with British forces.
- REGISTER NOW for our upcoming live webinar, How to Think Like a Threat Actor, in partnership with Uptycs.
- With just a few taps, people can see exactly where their money goes and catch problems early.
Using Virtual Payment Cards
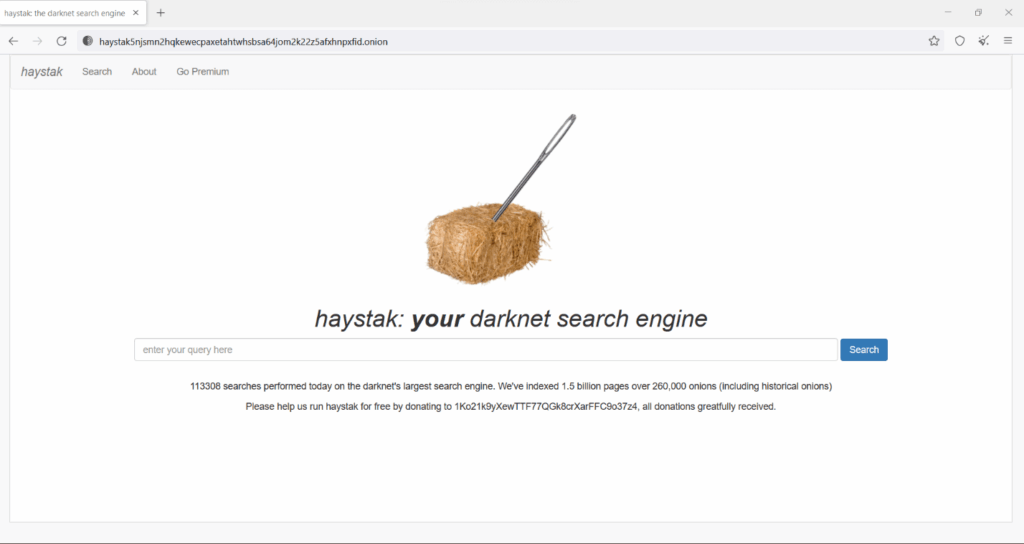
The dark web is a hidden layer of the internet that isn’t indexed by regular search engines and can only be accessed using special software like Tor. While it has legitimate uses, many illegal activities also take place there. One of the most common items sold on the dark web is stolen financial information, including credit card numbers. Mercedes-Benz revoked the token, removed the repository, and launched an internal investigation.
Category #1: Details Needed For Fraudulent Online Purchases
Cybercriminals can use this information to impersonate you, open fraudulent accounts under your name and make unauthorized transactions. BidenCash apparently used the free stolen data dump to draw attention for marketing, even using an image of President Biden as its brand identity, as discovered by Cyble researchers who detected the data breach. Use multifactor authentication to prevent threat actors from guessing at weak passwords, or getting into your systems with a brute force attack. MFA and strong password requirements will force your employees to use strong passwords and change them often. Stolen credit cards are also harmful to the businesses from which they were stolen in the first place.
The cards were published on an underground card-selling market, AllWorld.Cards, and stolen between 2018 and 2019, according to info posted on the forum. A virtual card is a payment method you can use for online and over-the-phone purchases without revealing your actual card/account data to the merchant. The card contains a randomly generated 16-digit number with an expiration date and CVV. While the virtual card is tied to your real account, the merchant or a potential hacker can’t access your actual bank details.
New Report On James Comey Suggests ‘ongoing Conspiracy’ Against Republicans, John Solomon Argues
A few years later, at the time of filming, he said his “plug”—the person through which he’d get his credit card information—was also only 14. Privacy is a BBB®-accredited company with a dedicated customer support team. As a company handling sensitive payment data, Privacy complies with PCI-DSS protocols and exceeds additional industry security standards to ensure the safety of your data. Get Privacy’s iOS or Android app on your phone and receive alerts and notifications of account activity to stay on top of any suspicious transactions. You can set spending limits on your Privacy Card to prevent overspending. You can also share your virtual card details with family members without revealing your underlying bank information.
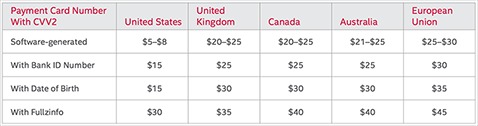
What’s The Worth Of Your Stolen Data?
Dutch cybersecurity firm EclecticIQ attributed the attacks to groups UNC5221, UNC5174, and CL-STA-0048. Attackers deployed web shells, reverse shells, and malware such as PlugX, KrustyLoader, SNOWLIGHT, VShell, and GOREVERSE. An exposed server tied to the campaign contained event logs and targeting lists, revealing both compromised assets and future plans. The Fars news agency reported that the attack targeted the bank’s infrastructure, disrupting online services, though officials expected to restore full service within hours. Users are urged to change passwords, enable multi-factor authentication, and watch for suspicious activity.
Acadian Ambulance Service
To minimize the risk of payment data exposure, only shop from reputable retailers, use digital payment methods or one-time private cards, and protect your accounts with two-factor authentication. Improve your online security by creating strong, unique passwords for your online banking and shopping accounts, using a password manager, and enabling multi-factor authentication (MFA) wherever possible. These practices will go a long way in reducing the risk of unauthorized access to your accounts. Stolen credit card numbers are often used for online shopping sprees or to make in-store purchases through digital wallets.
Data Breaches That Occurred In April 2024
When your card details are found, we immediately send an alert, allowing you to quickly take action, such as freezing your account or updating your card information. These criminals released the details of 740,858 credit cards, 811,676 debit cards, and 293 charge cards. The data dump disaster includes some complete names, expiration dates, CCV and unique email addresses. Detecting and preventing dark web credit card fraud can be difficult since the dark web is, by nature, hidden.
- Around the same time Qantas revealed a contact center breach impacting up to six million customers, caused by social engineering on external IT systems.
- The latest threat intelligence analysis, however, suggests those numbers are low.
- Although Workday did not directly name the group, security researchers linked the incident to ShinyHunters, which has run similar attacks against major companies including Adidas, Qantas, Allianz Life, Dior, Chanel, and Google.
- The incident involved access to more than 1.1 million private direct messages exchanged between users from February 2023 to July 2025.
- Okay, let’s examine how the initial verification works, using a real ‘config’ file shared by cybercriminals.
Intercepting Contactless Payments
Unless you live the rest of your life only paying with cash, you’ll never be totally impervious to payment fraud. Experts suggest that this giveaway serves as a marketing ploy to attract new users to B1ack’s Stash and establish its dominance in the competitive carding market. According to Security.org’s 2021 Credit Card Fraud Report, users with enabled alerts were more successful in preventing money loss than those without.
Carding Is A Cyber Crime Niche Of Its Own

“I’ve been able to get all-inclusive trips and holidays, and my Netflix accounts and Spotify,” D2 said. He showed off his account on Deliveroo, a British online food delivery company, where he had 65 credit cards saved. Using a public Wi-Fi network for payments is a major security risk as hackers can easily intercept the transmitted data. Unsecured Wi-Fi networks are prone to man-in-the-middle attacks, where a hacker intercepts the exchange between two parties—often by compromising the router—and gains access to sensitive data. Discover the pros and cons of using credit cards or card for purchases, including benefits and risks, to make informed financial decisions. Card checkers are tools used by threat actors to verify the validity and authenticity of credit card information they purchase on the dark web.
We can’t prove a direct correlation between this activity on Threads and the increased content moderation on Telegram following Pavel Durov’s arrest by French authorities in August. Cyble has acquired the leaked cc information and is available for its enterprise users as well as registered users at AmIBreached.com. From the data D3Labs has examined so far, about 30% appear to be fresh, so if this applies roughly to the entire dump, at least 350,000 cards would still be valid.
The ease of access and navigation of Telegram carding groups is a major concern, as it allows cybercriminals to easily buy and sell compromised payment card details. In this article, we’ll take a deep dive into some real-live techniques and scripts used by threat actors to commit credit card fraud. There are of course many ways to skin this proverbial feline, but it can be illuminating (possibly concerning) to see the actual steps involved. Let’s start right out with a step-by-step overview of the whole process, and then we’ll dive into some of the specific tools and methods that cybercriminals use in more detail. Post the dismantling of Joker’s Stash, cybercriminals displayed adaptability by establishing new marketplaces to fill the void, highlighting the resilience of criminal enterprises.
Plus, scammers do get caught—often ending up with a lengthy prison sentence or hefty fine. Most banks and credit card vendors offer you the option to receive fraud alert notifications—email or text alerts—warning you of potential card theft. Scammers start by prompting users to download malware, which is often disguised as a harmless email attachment. Once it starts running on your machine, the malware collects data such as used keystrokes, browser history, and shopping habits. Collecting used keystrokes is how hackers typically guess credit card numbers, PINs, and passwords.