However, note that Dark.fail monitors site uptime status and cannot tell whether the site is safe. To stay safe and private when visiting any listed sites, ensure you have a VPN and anti-malware installed and enabled. The search engine has indexed over 400,000 pages, and you can ask it to match your exact search term.
How To Access Dark Web Websites

The use of the dark web raises suspicion as it shows there is something you want to do privately. Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography.
Be Mindful Of Legal Implications
It may be difficult to have one framework that is applicable or valid for all countries. If the authorities see someone use Tor and, after some time, there is criminal activity in the area. Then their biggest lead would be to find the person who used the Tor browser. But there are definitely steps that can be taken to increase the monitoring of those who use dark web sites. SecureDrop is an open-source whistleblower submission system that news organizations can install to receive documents and tips from sources safely (and anonymously). Let’s break down what’s happening, what’s new, and what you should know especially if you’re researching or monitoring darknet activity for awareness or cybersecurity purposes.
But while anonymous email services can help protect your identity, they don’t make you immune to threats like email spoofing or social engineering. And it’s still essential to use strong passwords and two-factor authentication (2FA) to help keep your account secure. Although dark-web marketplaces utilize technologies like Tor and I2P to enhance anonymity, these methods are not foolproof. Law enforcement agencies continuously improve their ability to trace transactions and monitor marketplace activity. Abacus Market has emerged as one of the most reputable and widely used dark-web marketplaces in 2025.
As a result, it not only focuses on the UK but also provides worldwide news. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. The Excavator search engine digs through the depths of the dark web, offering an expansive view of indexed content. Haystak is a dark web browser that offers better filtering features that help users refine their search results, enabling them to locate exactly what they need. With its minimalist design, WormWeb aims to streamline the dark web experience, making it more accessible for users seeking a straightforward browsing experience. If cryptocurrency becomes more mainstream and widely adopted, it could have an impact on traditional financial institutions.
Weapons And Arms Trafficking Dark Web Statistics
Since academic research is often fenced off behind paywalls, Sci-Hub aims to democratize knowledge by allowing people to see publicly-funded research for free. In 2021, they showed how tax rates benefit the rich, and they relied on stolen or leaked IRS documents to do so. In addition to the surface web, ProPublica also hosts their site on the dark web, because they want to make sure that everyone can access their reporting. A robust antivirus can help block malware and other online threats, even on the dark web. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. Install Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online.
Constant Updates And Link Verification
Whether it’s evaluating the effectiveness of marketing software or the security features of digital wallets, our reviews are a reliable resource for those in the know. No, while the Tor network does host some websites that offer illegal goods or services, many sites are legitimate platforms dedicated to privacy, free speech, and open-source projects. With the increasing reliance on digital platforms for business operations, cybersecurity has become an integral part of any person’s or organization’s strategy. It can be very beneficial for users but there is also a very big downside. So that when a new visitor clicks on a link, their device is compromised. If used carefully it can provide a starting point for people who are looking to check out the dark side of the internet.
What Is Kubernetes And Containers? Why Is So Popular?

The dark web environment is notorious for hosting scam links, phishing clones, and honeypots designed to deceive visitors. Scam links may direct users to fraudulent marketplaces or services promising deals or products that never materialize, resulting in lost money or stolen credentials. Phishing clones are fake copies of legitimate dark web sites or marketplaces, created to harvest login details and personal information from unsuspecting users. Once you have the Tor Browser installed and optionally connected to a VPN, you can access the Hidden Wiki by entering its .onion URL directly into the browser’s address bar. Unlike regular websites, .onion addresses are long, complex strings of letters and numbers designed for anonymity and can be difficult to remember.
- Hidden networks also host a range of resources that can inform, educate, and support individuals who value anonymity.
- Dark web domains are generated in a cryptographically secure way, so they look like random strings of 16 characters or more (like 3g2upl4pq6kufc4m.onion, for example).
- Each category is further divided into multiple sub-categories for easy navigation.
- One of the primary reasons users prefer the Hidden Wiki and similar dark web directories over Google is privacy.
- Use your common sense to steer clear of online scams and illegal activity.
Dark Web Sites Offering Financial Services
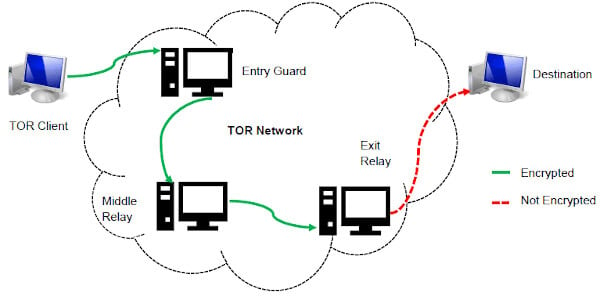
Instead, it represents a complex ecosystem where anonymity can serve both noble causes—such as protecting free speech and enabling investigative journalism—and darker ends. By approaching this hidden corner of the internet with informed caution and ethical awareness, you can navigate it more safely and responsibly. WeTheNorth is a Canadian market established in 2021 that also serves international users.
However, Ahmia doesn’t have a large developer supporting it, so it’s been the target of scams or cyberattacks in the past. Not to be confused with the riskier Hidden Wiki page, Wikipedia on Tor serves as a vast repository of information. You’ll find articles on a wide range of topics, such as history, science, and culture — and that’s just scratching the surface. Wikipedia manages one of the best Tor sites for encyclopedic knowledge. So take this guide as you explore where to go on the Tor Browser without risking your online security.
These tools add layers of privacy and protect against data leaks and surveillance. Password managers can help manage your credentials without compromising security. Many free VPN providers lack basic security features and track your online activity, so they don’t offer much privacy. That’s why it’s important to verify links through trusted directories and proceed with caution. While the best dark web sites listed above are a good starting point for a safe, legal surfing experience on Tor, there really is no substitute for a VPN.
Specialized Data Repositories
However, regulations that require cryptocurrency exchanges to comply with certain strict requirements can make it more difficult for journalists. To buy the documents they need, receive donations, or conduct other transactions anonymously. As a pretext to crack down on journalists and activists who are critical of their regimes. While it can be challenging to regulate the use of cryptocurrencies on dark web websites. Some countries have implemented stricter regulations on cryptocurrency exchanges. Requiring them to follow strict Know Your Customer policies and also Anti-Money Laundering policies.

While it’s a deep resource, it’s also illegal in many countries, because it may violate copyright restrictions, so check out the laws in your area before visiting. Proton Mail’s dark web version provides end-to-end encrypted email with enhanced privacy protection. The service doesn’t require personal information to create an account and works seamlessly through Tor. I found in my tests that all features work identically to the regular version. TorLinks maintains one of the most reliable directories of verified .onion sites. Its strength lies in regular updates and community-driven verification of links.