It’s important to know how these tools are used so you can perform reconnaissance and identify potential attacks or leaked information that can be used against you. Here is our list of 15 common technologies and tools used by cybercriminals to access and communicate via the dark web. Many users mostly rely on a dark web browser and secure Internet access to reach dark websites in that hidden part of the net. On iPhones, you’ll need some specialized apps and a good VPN for added protection.
Security Blogs
Therefore, you must run an IP leak test to ensure that the VPN is working completely fine and is not risking your digital security. The website allows visitors to view all the goods and services on display before they buy something. The quantity, price, and characteristics of the product are all provided. However, the platform lacks an advanced search option and a wallet-free payment option. The vendors aren’t required to register or apply for a vendor account while using this platform.
Browse The Dark Web Safely
Yes, it often deals with illegal content for illicit purposes in a hidden part of the web called dark web. Such activities are punishable and always risky for the security of your data. When trying to get access to the black market, it’s a good idea to use a separate computer or a dedicated virtual machine for dark web exploration.
Alternative Anonymous Networks
But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web. For example, the deep web is often a platform used by political activists who own a blog. But it also contains other news and religious sites, private discussion forums, and medical records. Pixel Privacy believes in digital privacy and does not believe in using it for heinous and/or illegal activities, and so the focus of this article will be on legal activities. The content of all these pages is stored on Google’s servers, but it’s mostly outdated, old content; smartphone app content; journals; court records; private social media profiles, and much more.
Countries differ in how aggressively they monitor Dark Web activity. In some authoritarian states, accessing Tor nodes can flag you for surveillance. The Darknet is a subset of the Internet operating over encrypted, anonymous overlay networks that require special software like Tor, Freenet, or I2P.
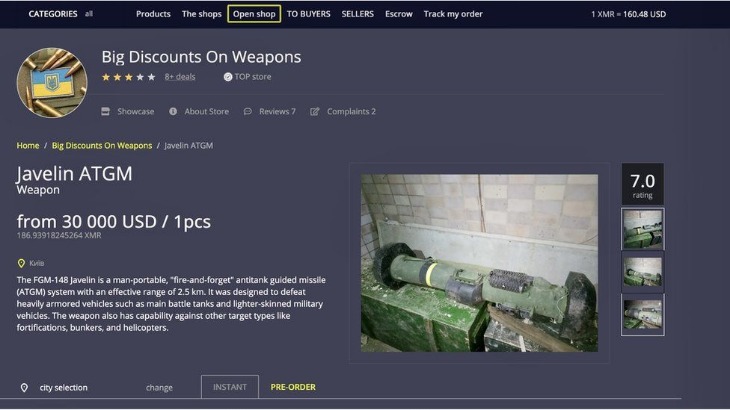
Products And Their Prices On Black Market

Black-market evolution mirrors the normal evolution of a free market, with both innovation and growth. The deep web, invisible web, or hidden web sounds like a mysterious depth of the world – but the concept is quite simple. The deep web is content on the World Wide Web not indexed by standard search engines. Think about search engines such as Google, Yahoo and Microsoft’s Bing, which give you results for indexed pages. They do this by following the links between sites and crawling the web’s threads like a spider.
Network Structure Of Transactions
More questionable digital content came into the trade, including malware and virus sales, purchasable vulnerability information and more. They found that to minimize risk, they would need to utilize end-to-end anonymity software, thus fostering a new iteration of digital black markets on a network colloquially termed the “dark web.” STYX MarketSTYX Market, launched in 2023, is all about financial crime.
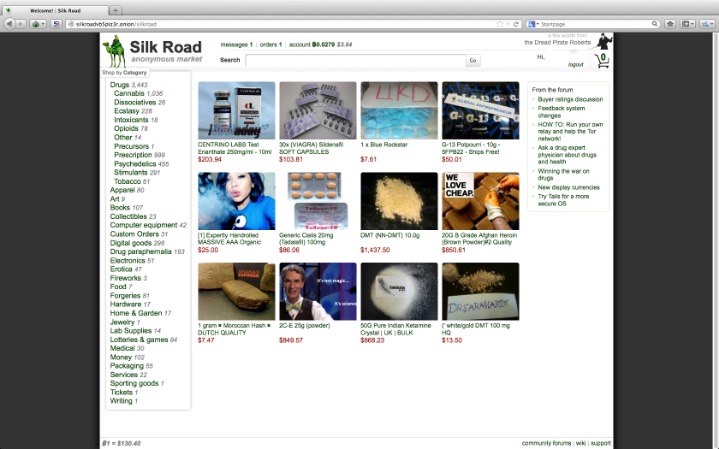
Silk Road And Early Markets
The Silk Road was founded in 2011 by Ross Ulbricht, who went by the alias “Dread Pirate Roberts.” Ulbricht envisioned a decentralized online marketplace free from government intervention. To achieve this, he leveraged Tor, a privacy-focused browser that masked users’ identities, along with Bitcoin for anonymous transactions. The CIA (Central Intelligence Agency) provides a .onion version of its website, enabling individuals to bypass restrictions to access its content from anywhere. This platform allows visitors to anonymously explore the World Factbook, submit information, apply for jobs, and perform any other actions available on the CIA’s main site. Sci-Hub provides free access to scientific papers, with millions of documents. Scientific journals often put their articles behind a paywall and charge high fees for access, but Sci-Hub offers open access to read or download research papers.
Install The Tor Browser
The US Naval Research Laboratory developed The Onion Routing (Tor) project in the late 90s. A network browser gives you access to sites with the ‘.onion’ registry operator. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship.
- At its peak, AlphaBay had over 400,000 users and facilitated transactions exceeding $1 billion.
- Dark markets often employ end-to-end encryption for communication between buyers and sellers, enhancing security and privacy.
- The exposed data included customer names, addresses, and purchase details.
- We first explore how the concept of currency evolved into a digital, anonymous form – a critical component of the modern vulnerabilities and illicit goods black market.
Simply accessing the dark web and using the Tor browser may already raise government suspicion. Anyone can access the dark web, and it’s not that complicated to do so. Just remember, if you want to explore the dark web, be very careful. This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware.
Leverage Free Cybersecurity Resources
Launched in 2021, Abacus Market caters primarily to English-speaking users. As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web. The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now). It’s somewhere Google and Bing don’t index, and you need special tools to get to it. Prior to Keeper, Darren served as an advisor to JiWire, now called NinthDecimal.

Security Links
- Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN.
- In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily.
- During 2016 and 2017, AphaBay becomes the dominant market (see Fig. 3), polarizing sellers around its own ecosystem, such that the fraction of multisellers decreases to 10% of all sellers until its closure.
- First, in the USA, it is a federal offense to use the USPS for any of these transactions.
- Dark web marketplaces are online platforms operating within the dark web, where individuals trade illicit goods and services while preserving their anonymity.
The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. Your ISP can’t see which websites you’re visiting on the dark web when you’re using Tor, but they might be able to predict or assume you are using Tor if they analyze your monitored internet traffic. The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online.
It is a useful tool for people who value their privacy and want to protect their communications with default end-to-end encryption, zero-access architecture, and minimal personal information requirements. Unfortunately, many dark web websites are devoted to the illegal trade of leaked personal information. If you’ve ever experienced an uptick in phishing attacks and spam after a data leak or breach, it may be because your personal information has been posted to the dark web. The dark web is shrouded in mystery, but not every onion website is dangerous.



